Endpoint Security Report
: Analysis on the Market, Trends, and TechnologiesWith the escalating number of cyber threats, endpoint security has emerged as a critical defense mechanism for organizations. Endpoints, which include laptops, smartphones, tablets, and other devices, are often the first line of defense against cyber attacks. Ensuring their security is crucial in protecting sensitive data, maintaining operational integrity, and safeguarding against breaches. This endpoint security report provides an in-depth analysis of the current landscape of endpoint security, highlighting the latest trends, funding details, and more. For example, significant investments and a workforce exceeding 135,000 employees in this sector suggest a strong market presence. Whether you are a cybersecurity professional, an IT manager, or a business leader, this report delivers insights into the current endpoint security landscape.
This article was last updated 413 days ago. If you find any info is missing, let us know!
Topic Dominance Index of Endpoint Security
The Dominance Index of Endpoint Security looks at the evolution of the sector through a combination of multiple data sources. We analyze the distribution of news articles that mention Endpoint Security, the timeline of newly founded companies working in this sector, and the share of voice within the global search data
Key Activities and Applications
- Threat Detection and Monitoring: Continuously monitoring endpoints for signs of malicious activity like malware infections and unauthorized access attempts using real-time threat detection tools and up-to-date threat intelligence.
- Endpoint Hardening: Configuring security settings, applying patches and updates, disabling unnecessary services, and ensuring secure configurations to reduce their attack surface.
- Data Encryption: Full disk encryption, file and folder encryption, and secure key management to protect sensitive data stored on endpoints from unauthorized access.
- Incident Response: Quickly and effectively respond to security incidents by containing the threat, eradicating the cause, and recovering affected systems.
- Access Control Management: Managing user accounts, implementing least privilege principles, and using multi-factor authentication (MFA).
- Endpoint Backup & Recovery: Regularly backing up data from endpoints and having a recovery plan in place to restore data in case of loss or corruption due to a security breach.
- Application Control: Prevents the execution of unauthorized or malicious software by implementing application whitelisting and blacklisting.
Emergent Trends and Core Insights
- Zero Trust Security: Operates on the principle of "never trust, always verify" model for strict identity verification and ensures that no implicit trust is given.
- Extended Detection and Response (XDR): Integrates multiple security products to deliver comprehensive threat detection and response across endpoints, networks, and cloud environments.
- Behavioral Analytics: Detects anomalies and potential threats based on the behavior of users and devices to mitigate attacks that may bypass traditional signature-based detection.
- Remote Work Security: Securing endpoints used by remote employees has become a critical focus to protect data on personal devices.
- Ransomware Defense: As ransomware attacks increase in frequency and sophistication, there is a heightened focus on integrating advanced threat detection, data backup and recovery solutions, and employee training to recognize phishing attacks.
- Unified Endpoint Management (UEM): UEM solutions provide a holistic approach to managing and securing mobile devices, desktops, and other IoT/connected devices.
- Privacy-Enhancing Technologies: Incorporating data masking, secure multi-party computation, and other techniques to protect sensitive data on endpoints and ensure data privacy and compliance.
Technologies and Methodologies
- AI and Machine Learning: AI and ML are used for threat detection, predictive analysis, and automated response, improving the speed and accuracy of security measures.
- Cloud-Based Endpoint Security: There is a growing trend towards cloud-based endpoint security solutions that offer scalability, ease of management, and real-time updates.
- Endpoint Detection and Response (EDR): Continuous improvements in EDR technologies provide more granular visibility, faster threat detection, and automated response.
- Antivirus & Anti-Malware Software: These programs detect, prevent, and remove malicious software from endpoints using signature-based detection, heuristics, and behavior analysis.
- Threat Intelligence Platforms (TIP): They gather, analyze, and share threat intelligence data from multiple sources to identify and respond to emerging threats.
Endpoint Security Funding
A total of 120 Endpoint Security companies have received funding.
Overall, Endpoint Security companies have raised $10.5B.
Companies within the Endpoint Security domain have secured capital from 314 funding rounds.
The chart shows the funding trendline of Endpoint Security companies over the last 5 years
Endpoint Security Companies
Uncover actionable market insights on 2.2K companies driving Endpoint Security with TrendFeedr's Companies tool.
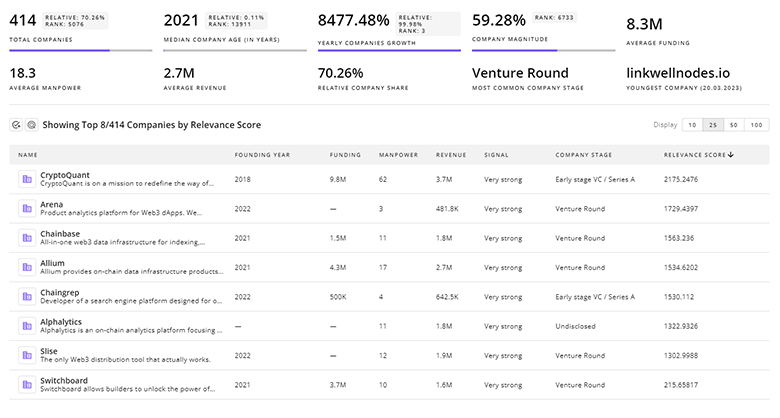
2.2K Endpoint Security Companies
Discover Endpoint Security Companies, their Funding, Manpower, Revenues, Stages, and much more
Endpoint Security Investors
Get ahead with your investment strategy with insights into 184 Endpoint Security investors. TrendFeedr’s investors tool is your go-to source for comprehensive analysis of investment activities and financial trends. The tool is tailored for navigating the investment world, offering insights for successful market positioning and partnerships within Endpoint Security.
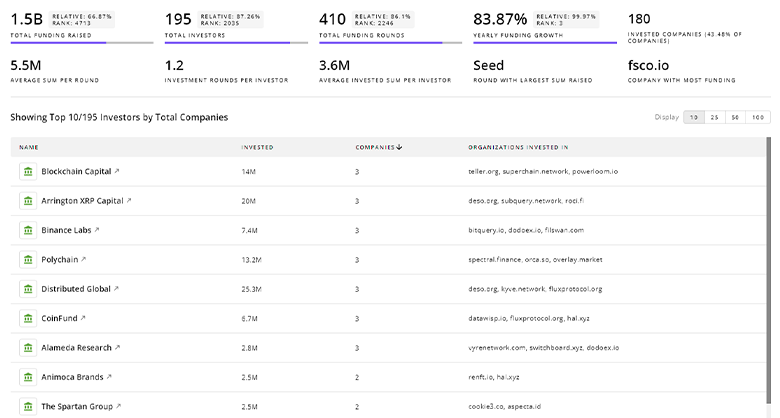
184 Endpoint Security Investors
Discover Endpoint Security Investors, Funding Rounds, Invested Amounts, and Funding Growth
Endpoint Security News
TrendFeedr’s News feature offers access to 9.3K news articles on Endpoint Security. The tool provides up-to-date news on trends, technologies, and companies, enabling effective trend and sentiment tracking.
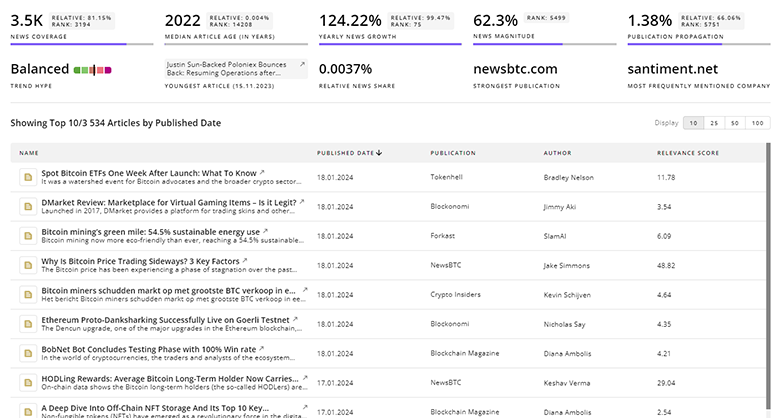
9.3K Endpoint Security News Articles
Discover Latest Endpoint Security Articles, News Magnitude, Publication Propagation, Yearly Growth, and Strongest Publications
Executive Summary
The endpoint security industry stands as a pivotal aspect of information security with a focus on network device and data protection. Marked by promising growth prospects and substantial financial backing, the sector is poised for future advancements. With a strong labor force and continued relevance in media and industry discussions, businesses are encouraged to prioritize endpoint security to uphold network integrity and safeguard their data assets.
Have expertise in trends or technology? Your input can enrich our content — consider collaborating with us!