Secure Communication Report
: Analysis on the Market, Trends, and TechnologiesThe secure communication landscape has experienced a striking 106.71% increase in topical prevalence over the past five years, driven by escalating data privacy concerns and stringent regulatory mandates. With the global market valued at USD 34.5 billion in 2024 and forecast to reach USD 65.2 billion by 2033, organizations are swiftly adopting advanced encryption and authentication solutions to safeguard sensitive interactions (https://www.verifiedmarketreports.com/product/secure-communication-market/).
103 days ago, we last updated this report. Notice something that’s not right? Let’s fix it together.
Topic Dominance Index of Secure Communication
To gauge the influence of Secure Communication within the technological landscape, the Dominance Index analyzes trends from published articles, newly established companies, and global search activity
Key Activities and Applications
- End-to-End Encryption: Ensures that only the sender and recipient can access message content, preventing service providers or intermediaries from decrypting communications (Smart Lock Messenger Secure & Convenient Access).
- Secure Data Transmission: Employs protocols such as TLS 1.3 and HTTPS to protect data in transit against interception and tampering (How Secure Data Transmission Enhances Business Connectivity in 2025).
- Authentication and Access Control: Verifies user and device identities—often via certificate-based or challenge-response methods—to prevent unauthorized entry into communication sessions.
- Secure File Sharing: Facilitates peer-to-peer or zero-knowledge file transfers with automatic expiration and audit trails to ensure documents remain confidential throughout exchange (Using Secure File Sharing to Provide Better Experience to Customers).
- Key Management and Distribution: Implements PKI-based key exchange, digital signatures, and tokenized key transport mechanisms to establish and rotate encryption keys securely.
Emergent Trends and Core Insights
- Rapid Market Expansion: The secure communication market is projected to nearly double from USD 34.5 billion in 2024 to USD 65.2 billion by 2033, reflecting enterprise and government investment in encryption and access controls.
- Messaging Security Surge: The messaging security segment is expected to grow from USD 9.38 billion in 2024 to USD 27.67 billion by 2033, driven by regulatory drivers (GDPR, HIPAA) and AI-enabled threat detection (Messaging Security Market Size | Grand View Research, 2024).
- Real-Time Monitoring & Compliance: Secure communication monitoring solutions are forecast to expand from USD 3.3 billion in 2025 to USD 13.7 billion by 2034, integrating anomaly detection with SIEM platforms for regulated industries (https://dimensionmarketresearch.com/report/secure-communication-monitoring-market/).
- Forward Secrecy Emphasis: Forward secrecy techniques are increasingly implemented to ensure that compromise of long-term keys does not expose past sessions, maintaining confidentiality over time.
- Hardware-Enhanced Security: Adoption of hardware security modules and TEEs for nonce generation and key storage is on the rise, offering tamper-resistant environments for cryptographic operations.
- Post-Quantum Readiness: Early movers are integrating quantum-resistant algorithms to future-proof encryption against emerging quantum threats, positioning themselves ahead of the anticipated shift to post-quantum cryptography.
Technologies and Methodologies
- AES-256 & TLS 1.3: Industry-standard symmetric encryption and transport protocols protect data in transit and at rest.
- AI-Driven Anomaly Detection: Machine learning models analyze communication patterns in real time to flag deviations and potential breaches.
- Blockchain for Integrity: Distributed ledger technology is explored for immutable audit trails and decentralized trust in message verification (https://www.datainsightsmarket.com/reports/secure-communication-1393333).
- Multi-Factor Authentication: Combines passwords, tokens, and biometric factors to strengthen user verification and reduce credential-based attacks.
- Zero-Knowledge Architectures: Ensures service providers cannot access user data by encrypting and decrypting content exclusively on client endpoints.
- Hardware Security Modules (HSMs): Dedicated devices perform cryptographic operations within secure enclaves, safeguarding keys and signatures from software vulnerabilities.
Secure Communication Funding
A total of 407 Secure Communication companies have received funding.
Overall, Secure Communication companies have raised $7.5B.
Companies within the Secure Communication domain have secured capital from 1.4K funding rounds.
The chart shows the funding trendline of Secure Communication companies over the last 5 years
Secure Communication Companies
- SecuQR: A privacy-first file sharing app that employs zero-knowledge encryption and QR-code–based exchange to anonymize both sender and receiver. Its lightweight, peer-to-peer design keeps data encrypted at rest and in transit, appealing to users who require anonymous, offline-capable file transfers.
- DropSecure: Provides real-time, zero-knowledge file transfer up to 2 GB using military-grade encryption at the source, ensuring no intermediate entity can decrypt data. Targeted at legal, financial, and healthcare professionals, it offers passwordless sharing with on-premise and branded deployment options.
- Cyph: A user-friendly secure communication platform offering end-to-end encrypted chat, video, and file sharing built by former SpaceX engineers. Cyph’s patent-pending protocol resists nation-state–level threat models and is open source, with automated key management to simplify adoption.
- ARMA Instruments: Offers a closed, zero-trust mobile communicator (G1 Secure Communicator) with fully secured OS and hardware layers. Designed to counter espionage by securing every system layer from application to hardware, ARMA targets defense and diplomatic use cases.
Get detailed analytics and profiles on 2.4K companies driving change in Secure Communication, enabling you to make informed strategic decisions.
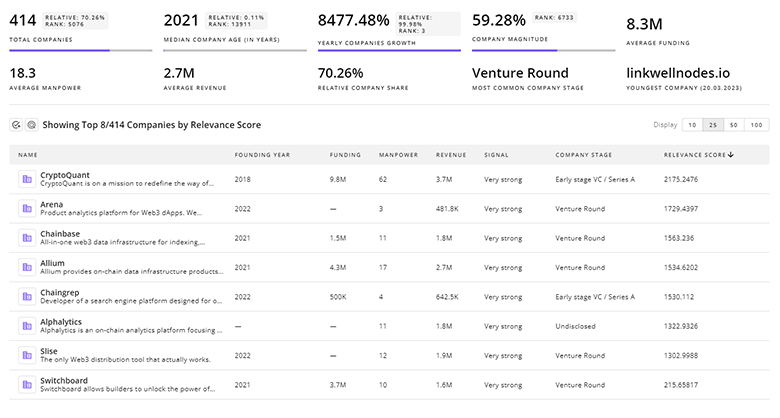
2.4K Secure Communication Companies
Discover Secure Communication Companies, their Funding, Manpower, Revenues, Stages, and much more
Secure Communication Investors
TrendFeedr’s Investors tool provides an extensive overview of 1.3K Secure Communication investors and their activities. By analyzing funding rounds and market trends, this tool equips you with the knowledge to make strategic investment decisions in the Secure Communication sector.
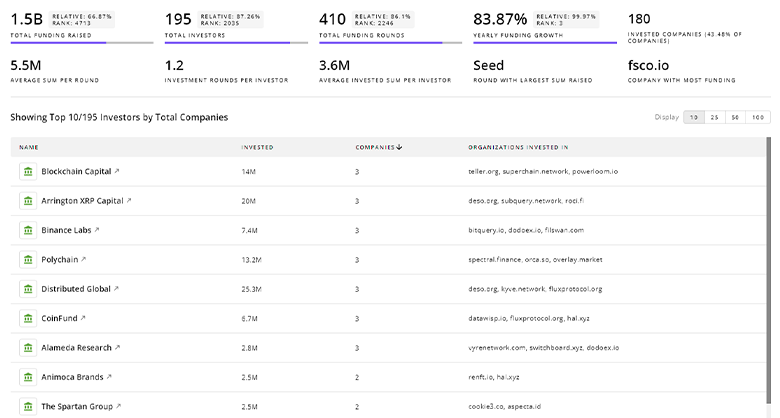
1.3K Secure Communication Investors
Discover Secure Communication Investors, Funding Rounds, Invested Amounts, and Funding Growth
Secure Communication News
Explore the evolution and current state of Secure Communication with TrendFeedr’s News feature. Access 3.2K Secure Communication articles that provide comprehensive insights into market trends and technological advancements.
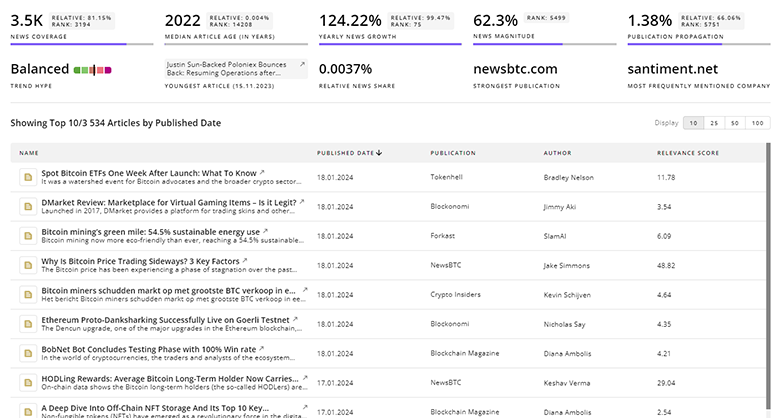
3.2K Secure Communication News Articles
Discover Latest Secure Communication Articles, News Magnitude, Publication Propagation, Yearly Growth, and Strongest Publications
Executive Summary
Secure communication has shifted from isolated encryption features to holistic platforms that unify messaging, file transfer, identity management, and hardware-based protections. Enterprises must evaluate solutions for end-to-end encryption, zero-knowledge architecture, and quantum resilience, while ensuring compliance with evolving regulations. Embracing AI-driven detection, hardware security modules, and adaptive authentication will be critical for defending against advanced threats. Organizations that prioritize integrated, future-proof communication ecosystems will maintain trust and confidentiality in an increasingly hostile digital environment.
We're looking to collaborate with knowledgeable insiders to enhance our analysis of trends and tech. Join us!