Vulnerability Management Report
: Analysis on the Market, Trends, and TechnologiesThe cybersecurity landscape is rapidly evolving, with a clear focus on vulnerability management as a critical aspect of protecting digital assets. The data indicates a robust ecosystem comprising 1348 companies, emphasizing the importance of cybersecurity due to the increasing reliance on technology and the surge in cyber threats. Key activities include identifying, classifying, prioritizing, remediating, and mitigating software vulnerabilities. There is significant growth in market interest and investment, with vulnerability management being closely related to sectors like cybersecurity, military & defense, and risk management. The field is marked by a 20.21% increase in news coverage and a 27.2% growth in funding over the past five years, signaling a positive trajectory in market engagement.
471 days ago, we last updated this report. Notice something that’s not right? Let’s fix it together.
Topic Dominance Index of Vulnerability Management
The Topic Dominance Index offers a holistic analysis of Vulnerability Management, merging data from 3 diverse sources: relevant published articles, newly founded companies, and global search metrics.
Key Activities and Applications
- Vulnerability Assessment and Penetration Testing (VAPT): Companies are offering services like VAPT to identify and address security weaknesses.
- Security Operations Centers (SOCs): Development and management of SOCs to provide 24/7 cybersecurity monitoring and response.
- Managed Security Services: Provision of ongoing security management and monitoring services for businesses of various sizes.
- Cybersecurity Training and Awareness: Initiatives to educate employees and stakeholders about cybersecurity best practices and threat mitigation.
- Compliance and Regulatory Advisory: Assisting organizations in meeting cybersecurity regulations and standards like ISO, GDPR, and PCI-DSS.
- Incident Response and Digital Forensics: Services to respond to and investigate cybersecurity incidents and breaches.
Emergent Trends and Core Insights
- Shift Towards Continuous Monitoring: A trend towards real-time and continuous monitoring of systems to detect and respond to threats promptly.
- Increased Focus on Supply Chain Security: Recognizing the importance of securing the software supply chain to prevent vulnerabilities from third-party components.
- Rise of Cybersecurity as a Service (CSaaS): Growth in CSaaS models, providing scalable and cost-effective cybersecurity solutions for businesses.
- Artificial Intelligence and Machine Learning: Leveraging AI and ML for advanced threat detection, vulnerability management, and predictive analytics.
- Remote Workforce Security: With the rise of remote work, companies are prioritizing solutions that secure distributed work environments.
Technologies and Methodologies
- Cloud Security: Solutions to protect cloud-based infrastructure and applications from cyber threats.
- Endpoint Protection: Advanced endpoint security platforms to prevent, detect, and respond to malware and other attacks.
- Zero Trust Architecture: Implementing Zero Trust principles to ensure strict access controls and verify all users and devices.
- Security Automation and Orchestration: Utilizing automation tools to streamline security operations and incident response workflows.
- Vulnerability Management Platforms: Development of platforms that offer comprehensive vulnerability assessment and prioritization.
Vulnerability Management Funding
A total of 158 Vulnerability Management companies have received funding.
Overall, Vulnerability Management companies have raised $4.4B.
Companies within the Vulnerability Management domain have secured capital from 415 funding rounds.
The chart shows the funding trendline of Vulnerability Management companies over the last 5 years
Vulnerability Management Companies
Stay connected with industry movements through TrendFeedr’s Companies tool, which covers 1.4K Vulnerability Management companies.
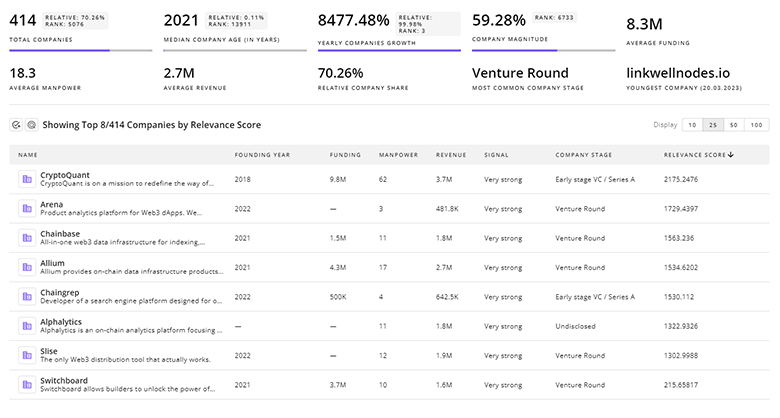
1.4K Vulnerability Management Companies
Discover Vulnerability Management Companies, their Funding, Manpower, Revenues, Stages, and much more
Vulnerability Management Investors
Discover investment patterns and trends with TrendFeedr’s Investors tool based on insights into 258 Vulnerability Management investors. This tool is essential for understanding the financial ecosystem of Vulnerability Management and developing successful investment strategies.
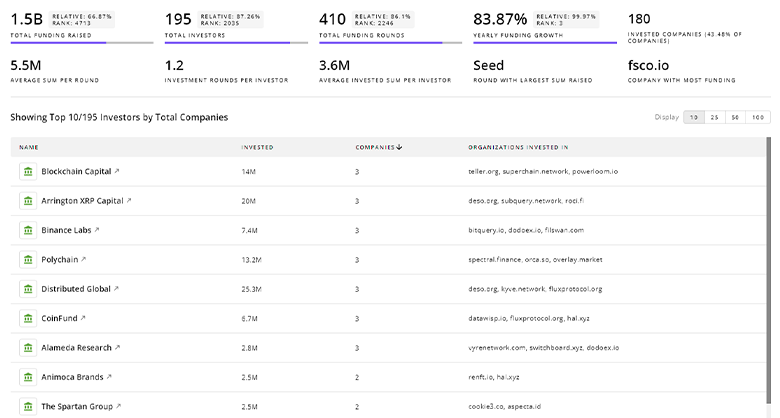
258 Vulnerability Management Investors
Discover Vulnerability Management Investors, Funding Rounds, Invested Amounts, and Funding Growth
Vulnerability Management News
TrendFeedr’s News feature grants you access to 6.5K Vulnerability Management articles. This tool supports professionals in tracking both past trends and current momentum in the industry.
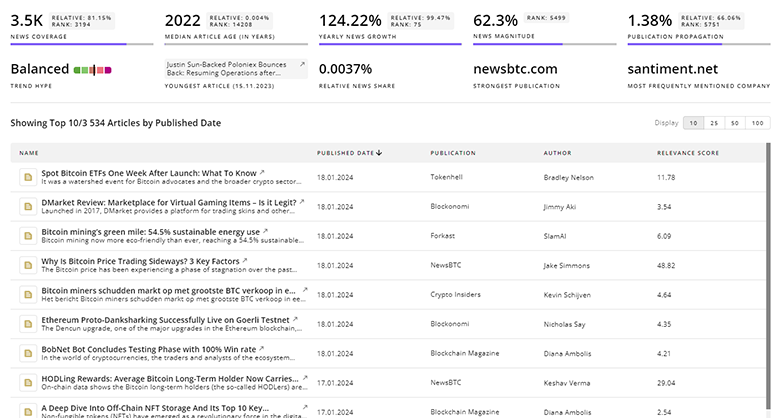
6.5K Vulnerability Management News Articles
Discover Latest Vulnerability Management Articles, News Magnitude, Publication Propagation, Yearly Growth, and Strongest Publications
Executive Summary
The cybersecurity domain, particularly vulnerability management, is experiencing significant growth and attention, driven by the need to combat escalating cyber threats. Companies are innovating with technologies like AI, ML, and cloud security to offer advanced solutions for real-time threat detection and response. The adoption of continuous monitoring, supply chain security, and CSaaS models reflects the industry's commitment to adapting to the changing landscape. As businesses continue to prioritize cybersecurity, the ecosystem is set to evolve with new trends and technologies, ensuring a secure digital future.
We're looking to collaborate with knowledgeable insiders to enhance our analysis of trends and tech. Join us!