Vulnerability Scanning Report
: Analysis on the Market, Trends, and TechnologiesThe shift from periodic to continuous, context-aware vulnerability scanning has created a high-growth commercial and technical landscape: 10,258 companies now work on vulnerability scanning, reflecting rapid market expansion and intense vendor competition. Scan frequency and severity both rise in parallel: recent industry analysis shows more organizations performing scans more often and a measurable uptick in critical-severity findings, forcing teams to prioritize risk-based workflows and automation to keep remediation velocity ahead of exploitation windows 2025 Vulnerability Statistics Report – Edgescan. The business implication is clear: buyers favor platforms that combine continuous discovery, exploit/context intelligence, and automated remediation orchestration, while smaller specialist vendors capture niche needs across cloud, API, container, and supply-chain scanning Frost Radar™: Vulnerability Management, 2023.
107 days ago, we last updated this report. Notice something that’s not right? Let’s fix it together.
Topic Dominance Index of Vulnerability Scanning
The Topic Dominance Index offers a holistic analysis of Vulnerability Scanning, merging data from 3 diverse sources: relevant published articles, newly founded companies, and global search metrics.
Key Activities and Applications
- Continuous external attack-surface discovery and monitoring (ASM/CTEM) to identify new assets and exposures as they appear; buyers expect real-time alerts and historical trend tracking to measure remediation velocity Detectify Hadrian.
- Network, host, and web application automated scanning (DAST/SAST/agentless host scans) to enumerate known CVEs and configuration weaknesses across hybrid estates Invicti.
- Software composition analysis (SCA) and supply-chain scanning to detect vulnerable open-source dependencies and provide remedial suggestions inside CI/CD pipelines Debricked Meterian.
- Risk-based prioritization that fuses exploit intelligence, asset criticality, and business context so teams fix the small subset of findings that cause most risk NopSec.
- Continuous penetration testing and PTaaS to validate findings, simulate attacker behavior, and provide human verification for complex business-logic issues Pentest as a Service market analysis.
- Automated remediation and patch orchestration targeting OS, third-party packages, container base images, and IaC templates to reduce time-to-fix and avoid developer friction Action1 Seal Security.
Emergent Trends and Core Insights
- Risk-driven scanning is mainstream. Vendors and buyers prefer prioritization models that combine CVSS/EPSS with real exploit telemetry and business context; this reduces remediation noise and drives resource allocation toward real risk Vulnerability Management Growth Opportunities.
- Continuous monitoring replaces quarterly cycles. Market commentary and survey data show a material shift toward scanning frequencies that approach continuous assessment for externally facing assets and critical internal services 5 Key Vulnerability Management Trends MSPs Should Consider in 2025 – ConnectSecure IDC PlanScape: Vulnerability Management.
- AI and automation move from detection to decisioning. Machine learning now reduces false positives, predicts exploitability, and automates triage; vendors advertise prioritization lifts and faster remediation cycles tied to AI-assisted workflows.
- Expanded scope: cloud misconfigurations, APIs, containers, and IaC are first-class scan targets. Scanners evolve to include IaC linters, image scanning, and API fuzzing as standard modules.
- Platform consolidation plus specialization. Large vendors bundle discovery, prioritization, and remediation while specialists own niches (SCA, OPC UA scanners, API fuzzers, exploit intelligence), creating partnership and acquisition activity as a dominant competitive dynamic Vulnerability Management Market, Global, 2024–2029.
- Commercial pressure and regulatory drivers increase buyer urgency. Compliance mandates and higher expected cyber losses push firms toward managed VM and VMaaS models, supporting MSSP channel growth Worldwide Device Vulnerability Management Market Shares, 2022.
Technologies and Methodologies
- Agentless and agent-based scanning engines. Agentless scans remain valuable for quick discovery and external posture checks; agents support continuous host and endpoint telemetry where required.
- DAST, SAST, IAST, and SCA combined into CI/CD pipelines. Shift-left toolchains embed security earlier and produce developer-friendly remediation guidance inside pull requests GitLab vulnerability report.
- Container and image scanners plus runtime protection. Image scanning catches known CVEs pre-deploy; runtime agents and behavioral detectors catch novel exploitation during execution.
- IaC scanners and policy linters for Terraform/CloudFormation/Kubernetes manifests to prevent misconfiguration drift.
- AI/ML for triage, predictive exploit scoring, and automated remediation orchestration; many patents and vendor roadmaps point to predictive risk engines and intelligent plug-in scheduling to cut false positives and scan time.
- Hybrid testing: automated scanning plus human validation (PTaaS, red team) to cover business logic and complex attack paths that scanners miss BreachLock recognition in Gartner Hype Cycle.
Vulnerability Scanning Funding
A total of 553 Vulnerability Scanning companies have received funding.
Overall, Vulnerability Scanning companies have raised $17.5B.
Companies within the Vulnerability Scanning domain have secured capital from 1.8K funding rounds.
The chart shows the funding trendline of Vulnerability Scanning companies over the last 5 years
Vulnerability Scanning Companies
- HostedScan Security — HostedScan provides continuous, open-source based scanning with 24x7 alerts and dashboards that consolidate OpenVAS, OWASP ZAP, and Nmap outputs into a single view; it targets small IT teams that need always-on detection without heavy integration work. Its product emphasizes simple deployment and automated change alerts so security owners spot new exposures quickly.
- Vulnerabbit — Vulnerabbit offers an AI-powered platform that combines web application and cloud infrastructure scanning with context-aware remediation plans and low false-alarm claims; it positions itself as a developer-friendly scanner that translates findings into executable fixes. The vendor focuses on automation that integrates into CI/CD pipelines and on reducing analyst overhead through intelligent triage.
- Scan0 Software — Scan0 targets cloud-native runtime security, providing behavioral intelligence and automated threat prevention for Kubernetes and containerized workloads; it combines runtime detection with supply-chain visibility to detect zero-day and exploit activity in production. Its specialization helps security teams that need runtime context beyond static CVE lists.
- Molemmat / OpalOPC — OpalOPC concentrates on industrial control and OPC UA-specific vulnerability scanning, producing easy-to-consume reports and correction suggestions for OT environments; it fills a niche where traditional IT scanners lack protocol knowledge and safe OT scanning methods. Organizations that run manufacturing or critical infrastructure gain targeted coverage for industrial protocols.
- Fitoxs — Fitoxs provides a compact, API and web app scanner with a large test corpus (10,000+ checks), automated exploitation evidence, and CI/CD integrations; it serves SMBs and regional customers that require high-accuracy DAST with low setup friction. The product blends automated exploit attempts with vulnerability management features to accelerate developer remediation.
Stay connected with industry movements through TrendFeedr’s Companies tool, which covers 10.1K Vulnerability Scanning companies.
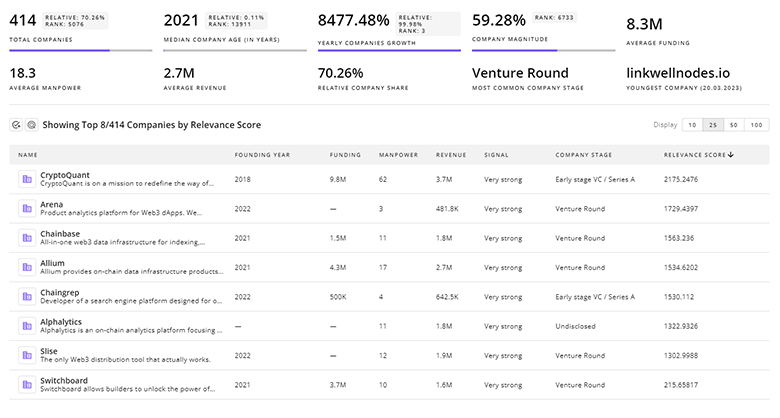
10.1K Vulnerability Scanning Companies
Discover Vulnerability Scanning Companies, their Funding, Manpower, Revenues, Stages, and much more
Vulnerability Scanning Investors
Discover investment patterns and trends with TrendFeedr’s Investors tool based on insights into 2.2K Vulnerability Scanning investors. This tool is essential for understanding the financial ecosystem of Vulnerability Scanning and developing successful investment strategies.
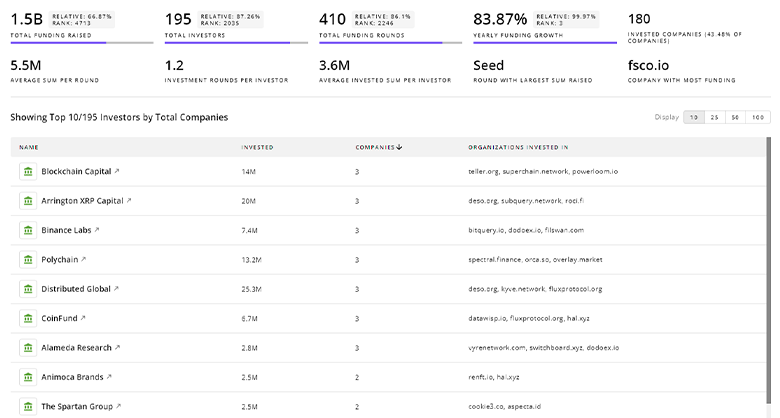
2.2K Vulnerability Scanning Investors
Discover Vulnerability Scanning Investors, Funding Rounds, Invested Amounts, and Funding Growth
Vulnerability Scanning News
TrendFeedr’s News feature grants you access to 6.3K Vulnerability Scanning articles. This tool supports professionals in tracking both past trends and current momentum in the industry.
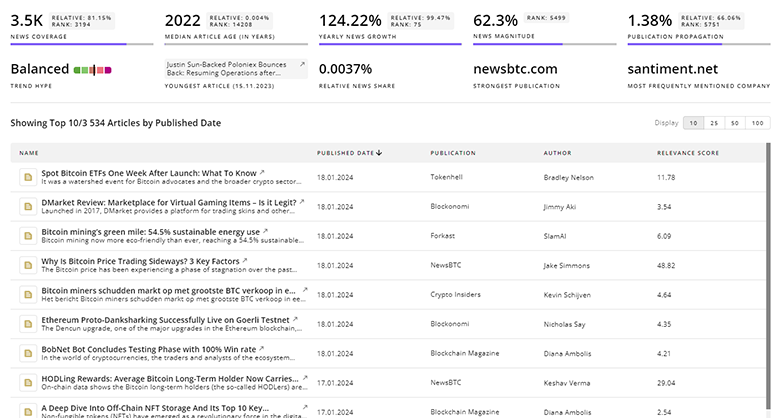
6.3K Vulnerability Scanning News Articles
Discover Latest Vulnerability Scanning Articles, News Magnitude, Publication Propagation, Yearly Growth, and Strongest Publications
Executive Summary
Vulnerability scanning now sits at the intersection of continuous discovery, risk intelligence, and remediation automation. The market has grown both broad and deep: thousands of vendors serve distinct slices of the problem set while platform vendors converge functionality to simplify buyer decisions. For practitioners, the operational priorities are clear: adopt continuous external discovery, integrate SCA and IaC checks into CI/CD, apply exploit/context intelligence for prioritization, and automate safe remediation orchestration where possible. For vendors and investors, the commercial opportunity favors solutions that combine high-quality data, predictive risk scoring, and low-friction developer workflows; firms that deliver measurable reductions in time-to-remediate and demonstrable business risk reduction will capture the next wave of enterprise adoption.
We're looking to collaborate with knowledgeable insiders to enhance our analysis of trends and tech. Join us!