Attack Surface Management Report
: Analysis on the Market, Trends, and TechnologiesThe attack surface management market is at a decisive inflection point: total market value was approximately $900,000,000 in 2024 and the internal trend data projects $3.3 billion by 2029 (CAGR 29.3%), signalling rapid demand for continuous visibility and remediation capabilities. Market research outside the internal dataset reports broadly similar expansion estimates (for example, TechSci forecasts a 28.42% CAGR through 2030 and Fortune Business Insights reports a 2024 market value near $856.5M with a 22.6% CAGR to 2032), reinforcing that ASM growth rests on cloud adoption, multi cloud complexity, and higher attacker sophistication techsciresearch.com. The practical implication is that security teams will shift budget and headcount toward always on discovery, AI risk scoring, and toolchain integration that ties ASM outputs to detection and response workflows.
This report was last updated 96 days ago. Spot an error or missing detail? Help us fix it by getting in touch!
Topic Dominance Index of Attack Surface Management
To identify the Dominance Index of Attack Surface Management in the Trend and Technology ecosystem, we look at 3 different time series: the timeline of published articles, founded companies, and global search.
Key Activities and Applications
- Continuous external asset discovery and inventory — automated discovery of domains, subdomains, IP blocks, certificates, exposed cloud services, and shadow IT to build an attacker-view inventory; this remains the foundational ASM activity and drives follow-on detection work marketresearch.com.
- Real-time risk scoring and prioritization — AI/ML evaluates exploitability, business criticality, and likely attacker paths so remediation targets highest risk assets first, reducing mean time to remediation and SOC load.
- Continuous Threat Exposure Management (CTEM) — end-to-end workflows that discover exposures, validate exploitability (sometimes via automated red team or BAS), and measure exposure reduction over time to quantify security improvement marketresearch.com.
- Third-party and supply chain exposure monitoring — continuous scanning of vendor domains, cloud footprints, and managed services to detect transitive risk and triage remediation with procurement and vendor teams zionmarketresearch.com.
- API and SaaS posture assessment — discovery and verification of undocumented APIs, misconfigured SaaS connectors, and exposed keys that create business-critical avenues for attackers.
- Integration with SecOps (XDR, SIEM, SOAR) — ASM feeds prioritized findings into detection and response playbooks to accelerate containment and to reduce false positives by adding external context.
Emergent Trends and Core Insights
- AI-native discovery and predictive scoring — vendors embed ML models to infer asset ownership, map attack paths, and predict which exposures attackers will exploit next; this changes ASM from cataloging to forecasting risk.
- Convergence with detection platforms - ASM outputs increasingly feed and fuse with XDR and SIEM platforms so detection, investigation, and mitigation operate from the same asset reality; buyers prize platforms that reduce tool fragmentation.
- From point-in-time scans to continuous validation — continuous automated red teaming and breach and attack simulation validate that discovered issues are exploitable and confirm remediation efficacy, shifting vendor differentiation to continuous validation capabilities.
- Expanded scope: identity, data, OT and IoT — ASM now commonly includes identity attack surface management and data layer exposure detection while also extending coverage to OT/ICS and IoT endpoints that sit outside traditional IT asset inventories helpnetsecurity.com.
- Regional dynamics and customer segmentation — North America leads adoption, APAC grows fastest as multi cloud use rises, and regulated sectors such as BFSI, government, and critical infrastructure buy first and buy higher tiers of automation.
Technologies and Methodologies
- ML and graph-based attack path modeling — graph analytics connect discovered assets, identities, and vulnerabilities to show realistic lateral movement and prioritise remediation by business impact.
- Passive DNS, certificate transparency and wide-scale reconnaissance engines — these data sources reveal forgotten domains, staging environments, and expired certificates that create exposures.
- Event-driven scanning and CI/CD integration — scanners trigger on code or infra changes so discovery remains aligned to engineering velocity and reduces time between exposure creation and detection.
- Automated red teaming and BAS (PTaaS) — adversary simulation pipelines test whether discovered weaknesses are exploitable and produce repeatable metrics to show security program improvement watchtowr.com.
- Digital twin and live environment replicas — early patent activity and R&D point to maintaining synchronized replicas of IT estates for risk forecasting and safe testing of reconfiguration strategies.
Attack Surface Management Funding
A total of 134 Attack Surface Management companies have received funding.
Overall, Attack Surface Management companies have raised $5.8B.
Companies within the Attack Surface Management domain have secured capital from 545 funding rounds.
The chart shows the funding trendline of Attack Surface Management companies over the last 5 years
Attack Surface Management Companies
Cyble
Cyble provides an AI-centric ASM capability focused on external asset discovery, dark web intelligence, and automated alerting; the company emphasizes attacker-view reconnaissance and uses ML to reduce false positives and speed analyst triage. Cyble's positioning helps security teams prioritize incidents that have clear exploitation paths.RiskProfiler
RiskProfiler concentrates on External Attack Surface Management with live exposure maps and context linking assets to business processes; its messaging highlights continuous, context-aware monitoring that aligns ASM outputs to operational owners. The platform targets organizations that need asset-to-business visibility for governance.Trend Micro
Trend Micro has extended its Vision One stack with Attack Surface Risk Management features that combine cloud inventory, generative AI summaries, and automated remediation workflows; this reflects the vendor trend of folding ASM into larger detection and response suites. Trend Micro's reach into existing enterprise customers makes it a practical option for buyers seeking consolidated tooling.Bitsight
Bitsight couples ASM capabilities with third-party risk monitoring and continuous automated scanning; the vendor emphasizes risk-prioritized exposure reduction and vendor risk scoring that helps procurement and security teams manage supply-chain exposures. Bitsight targets customers that need correlation of external exposures with vendor performance metrics.FortifyData
FortifyData provides an ASM analytics layer that aggregates multi cloud asset data, offers AI risk scoring, and supplies market and regional insights for strategic planning; the company focuses on analytics and reporting for security leadership and engineering teams. This positioning appeals to organizations that demand evidence-based risk metrics for board and CISO reporting.
Identify and analyze 651 innovators and key players in Attack Surface Management more easily with this feature.
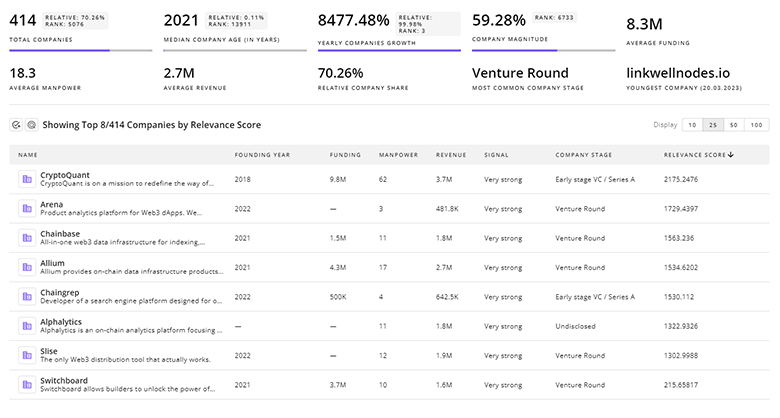
651 Attack Surface Management Companies
Discover Attack Surface Management Companies, their Funding, Manpower, Revenues, Stages, and much more
Attack Surface Management Investors
TrendFeedr’s investors tool offers a detailed view of investment activities that align with specific trends and technologies. This tool features comprehensive data on 812 Attack Surface Management investors, funding rounds, and investment trends, providing an overview of market dynamics.
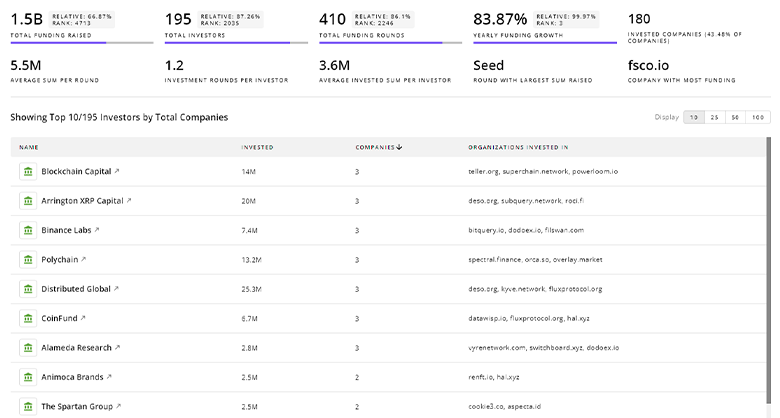
812 Attack Surface Management Investors
Discover Attack Surface Management Investors, Funding Rounds, Invested Amounts, and Funding Growth
Attack Surface Management News
Stay informed and ahead of the curve with TrendFeedr’s News feature, which provides access to 1.8K Attack Surface Management articles. The tool is tailored for professionals seeking to understand the historical trajectory and current momentum of changing market trends.
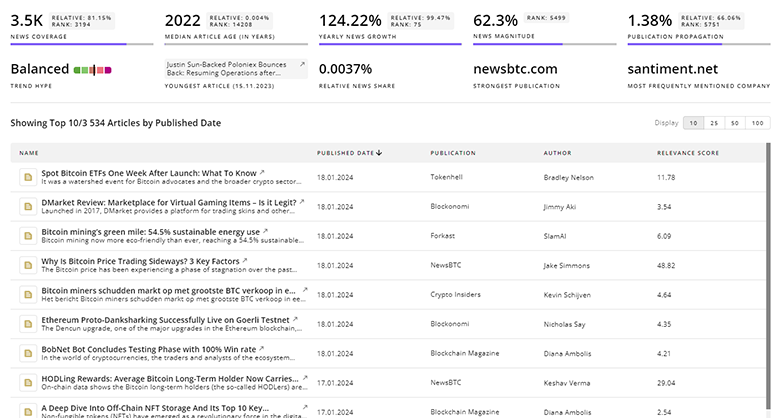
1.8K Attack Surface Management News Articles
Discover Latest Attack Surface Management Articles, News Magnitude, Publication Propagation, Yearly Growth, and Strongest Publications
Executive Summary
ASM has moved from a niche reconnaissance activity to a core security capability driven by cloud proliferation, multi cloud complexity, and attacker tactics that exploit external and unmanaged assets. The evidence indicates rapid commercial growth and buyer appetite for continuous, AI-driven discovery, prioritized remediation, and integrations with detection and response tooling. Security leaders should treat ASM as a foundational input to vulnerability prioritization, third-party risk processes, and CTEM programs. Vendors that win will prove continuous measurement of exposure reduction, reduce analyst toil through accurate prioritization, and offer clear integration paths into SecOps workflows. The window to capture market share is now; decisions that accelerate integration, telemetry coverage, and validated remediation will determine long term market leadership.
Interested in enhancing our coverage of trends and tech? We value insights from experts like you - reach out!