
Digital Security Report
: Analysis on the Market, Trends, and TechnologiesThe digital security landscape is accelerating toward identity-centric, data-centric defenses as spending and technology adoption climb: the internal digital security data shows a 16.0% CAGR for the market and a projected market value of $109.9 billion by 2030, forcing firms to prioritize continuous identity verification, cryptographic agility, and cloud-native controls to reduce rising breach costs and the explosive volume of alerts Cybersecurity trends: IBM’s predictions for 2025.
We updated this report 90 days ago. Noticed something’s off? Let’s make it right together — reach out!
Topic Dominance Index of Digital Security
The Topic Dominance Index trendline combines the share of voice distributions of Digital Security from 3 data sources: published articles, founded companies, and global search
Key Activities and Applications
- Automated, AI-driven threat hunting and triage that reduces mean-time-to-detect by prioritizing high-risk signals and automating containment workflows
- Identity fabric consolidation: unifying user, machine, and device identities across clouds and SaaS with continuous authentication and dynamic trust scoring to enable Zero Trust at scale
- Supply-chain integrity (SBOM generation and continuous verification) to prevent insertion of vulnerable components and meet tightening regulatory mandates
- Confidential computing and hardware-root attestation to protect data in use and reduce insider and hypervisor risks, especially in finance and healthcare Protecting Health: Cybersecurity in Medical Devices.
- Decentralized key management and crypto-agility initiatives to prepare for post-quantum migration and to remove single points of cryptographic failure
Emergent Trends and Core Insights
- Alert overload becomes the primary operational failure mode; vendors that convert high volumes of telemetry into ranked, actionable incidents and automated containment gain outsized operational value.
- Identity as the enforcement plane: enterprises move from device/network perimeter controls to continuous, context-aware identity scoring (behavioral signals, transaction velocity, device posture) for every access decision Digital Trust Market Research Report.
- Crypto-asset and certificate visibility: organizations need full inventories of keys and certificates to achieve crypto agility and avoid large-scale expiry or PQC migration disruption
- Convergence of IT and OT security: securing analog-to-digital interfaces and legacy industrial sensors becomes a strategic necessity for critical infrastructure and manufacturing.
- Regulatory and geo-sovereignty fragmentation drives vendor selection: platforms that provide verifiable residency, audit trails, and localized compliance reporting win in regulated sectors
Technologies and Methodologies
- eBPF and kernel-level observability for low-latency, high-fidelity host and network telemetry that scales in cloud native deployments.
- Graph databases and relationship mapping to detect multi-stage attack chains that linear log analysis misses.
- SOAR 2.0 with predictive decisioning and cross-organization playbooks to automate containment across hybrid estates and partner slices
- Adversarial ML defenses and data provenance controls to protect security models from poisoning and to ensure forensic reliability of telemetry.
- Confidential computing (TEE), hardware attestation, and embedded root-of-trust to protect workloads and device identities from low-level compromise.
Digital Security Funding
A total of 275 Digital Security companies have received funding.
Overall, Digital Security companies have raised $11.6B.
Companies within the Digital Security domain have secured capital from 936 funding rounds.
The chart shows the funding trendline of Digital Security companies over the last 5 years
Digital Security Companies
-
Authzed
Authzed offers fine-grained authorization as a service based on a relationship-graph model that simplifies complex permission logic for microservices. The service reduces developer effort to implement context-aware access control and accelerates safe scaling of multi-tenant applications while enforcing consistent policies across clouds. -
Crypto-Certs (Cryptosense)
Cryptosense (presented here as Crypto-Certs) scans and maps cryptographic assets—certificates, keys and algorithms—and produces risk scores tied to PQC migration planning. Its tooling helps security teams identify legacy ciphers and certificates at risk of mass expiry or incompatibility during algorithm swaps, supporting crypto-agility programs. -
Immuta
Immuta enforces dynamic data access policies at the query level across multi-cloud data platforms, enabling data teams to access governed datasets without moving data. The platform automates masking, anonymization, and policy enforcement to meet digital sovereignty requirements while preserving analytic productivity. -
Physec
Physec embeds device-centric security into edge and embedded systems to secure the analog-digital interface, targeting brownfield industrial deployments. Its approach addresses the significant vulnerability that legacy sensors and non-networked devices introduce to OT environments.
Gain a better understanding of 3.2K companies that drive Digital Security, how mature and well-funded these companies are.
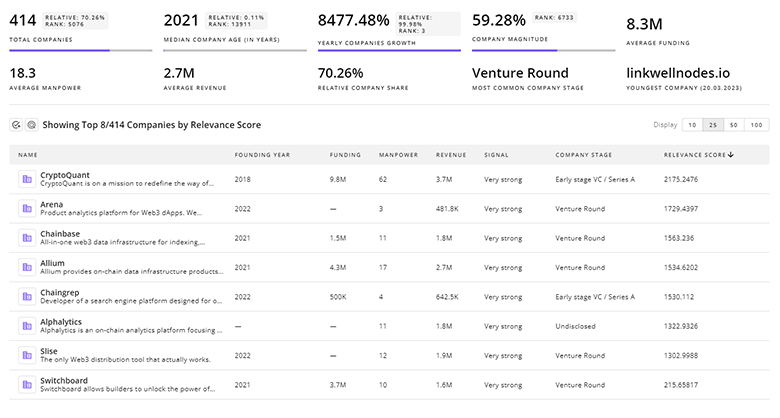
3.2K Digital Security Companies
Discover Digital Security Companies, their Funding, Manpower, Revenues, Stages, and much more
Digital Security Investors
Gain insights into 1.2K Digital Security investors and investment deals. TrendFeedr’s investors tool presents an overview of investment trends and activities, helping create better investment strategies and partnerships.
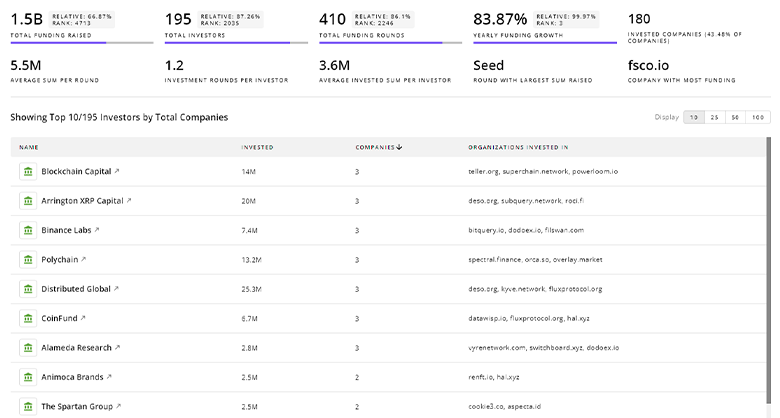
1.2K Digital Security Investors
Discover Digital Security Investors, Funding Rounds, Invested Amounts, and Funding Growth
Digital Security News
Gain a competitive advantage with access to 4.9K Digital Security articles with TrendFeedr's News feature. The tool offers an extensive database of articles covering recent trends and past events in Digital Security. This enables innovators and market leaders to make well-informed fact-based decisions.
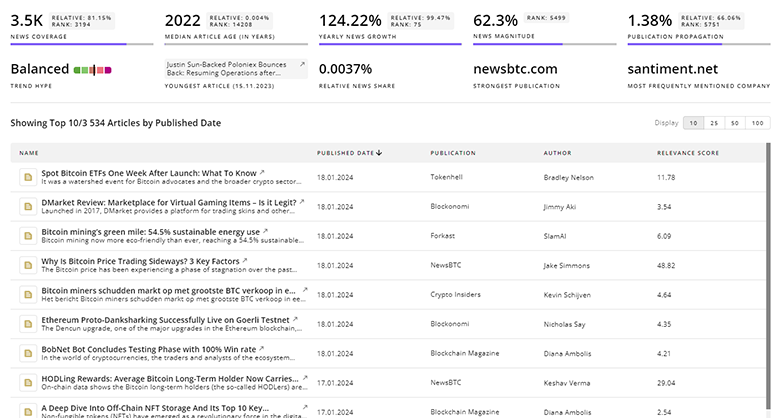
4.9K Digital Security News Articles
Discover Latest Digital Security Articles, News Magnitude, Publication Propagation, Yearly Growth, and Strongest Publications
Executive Summary
The business imperative in digital security is clear: treat identity, cryptography, and data provenance as primary control planes rather than auxiliary capabilities. Market growth rates and forecasts show sustained investor and buyer appetite, but operational constraints—alert volume, legacy estate complexity, and skills shortages—will determine winners and losers. Firms that pair continuous identity verification, crypto-asset visibility, and automated containment with hardware-anchored trust will reduce dwell time and regulatory exposure. Vendors should focus R&D and go-to-market efforts on pragmatic crypto-agility, supply-chain verification, and machine-centric identity solutions that integrate with customers’ cloud and OT estates; buyers should prioritize platforms that measurably lower incident remediation time while documenting compliance for increasingly divergent regional regulations.
We seek partnerships with industry experts to deliver actionable insights into trends and tech. Interested? Let us know!











