Mobile Device Security Report
: Analysis on the Market, Trends, and TechnologiesThe mobile device security market is expanding fast: total market value reached USD 9.36 billion in 2023 and the internal trend data projects USD 22.64 billion by 2029, reflecting sustained enterprise demand for mobile-first protections. Enterprises report high incident rates that drive budgets—45% of organizations said a mobile device incident caused data loss or downtime, and 73% of those rated the impact as major 2022 Mobile Security Index – Executive Summary. Consumer expectations also matter: device features such as identity protection and security updates score heavily in buyer decisions, with industry testing showing leading consumer devices still leave phishing unblocked in manual-craft attack scenarios Mobile Device Security 2022 – Omdia. The consequence is clear: vendors that combine continuous device posture, AI-driven detection, and integrated MDM/MTD controls will capture the fastest growth as adoption shifts from point products to platform solutions.
We last updated this report 3 days ago. Tell us if you find something’s not quite right!
Topic Dominance Index of Mobile Device Security
To gauge the impact of Mobile Device Security, the Topic Dominance Index integrates time series data from three key sources: published articles, number of newly founded startups in the sector, and global search popularity.
Key Activities and Applications
- Mobile Device Management (MDM) and UEM: centralized provisioning, zero-touch enrollment, policy enforcement and fleet monitoring for corporate and BYOD devices, driving the large enterprise and SME use cases.
- Mobile Threat Defense (MTD): continuous, on-device detection of malware, phishing and network threats plus automated remediation to protect endpoints in real time.
- Mobile Application Security: SAST/DAST/IAST, supply-chain vetting, and runtime shielding (RASP/app shielding) to prevent tampering, data leakage and reverse engineering in finance and healthcare apps.
- Identity and Access: passwordless, biometric and device-bound authentication plus continuous verification for zero-trust access from mobile endpoints Proximia.
- Secure Mobile Communications and Payments: end-to-end encryption, anti-SIM-swap protections and tokenization for payments and sensitive messaging.
- Forensics and Incident Response: rapid extraction, telemetry analysis and legal-grade evidence collection for high-impact breaches and fraud investigations.
Emergent Trends and Core Insights
- AI becomes operational security. Vendors embed ML models for anomaly detection, predictive threat scoring and automated triage, shifting value from signature engines to behavioral analytics.
- Zero-trust expands into mobile posture. Continuous device posture checks and contextual access decisions replace one-time logins, aligning MDM/UEM with identity systems.
- Privacy-first threat telemetry. Solutions favor on-device analysis and aggregated risk reporting to meet GDPR/CCPA constraints while preserving detection fidelity.
- Shift from app hardening to integrated app supply-chain risk management. Automated SAST/DAST in CI/CD and SBOM monitoring appear as standard controls for regulated verticals.
- Network-level protections edge into handset space. Secure overlay networking, multipath encryption and stealth networking target SIM-swap, interception and 5G slicing risks Dispersive Holdings, Inc..
- Market signals and growth divergence. Core market figures vary by segment: mobile-security software is in the ~$9.4bn range (2023 internal data) with high single-digit to double-digit CAGRs reported across subsegments (MDM/UEM, MTD, app security), creating distinct routes to scale for platform vendors and niche specialists Global Mobile Device Management Market Size, Share, Trends & Growth Forecast Report.
Technologies and Methodologies
- Trusted Execution Environments and Secure Elements: hardware anchors for key storage, attestation and credential protection; vendors emphasize eSIM/eSE and secure enclaves for cryptographic trust SHLD-X GmbH.
- Runtime Application Self-Protection (RASP) and App Shielding: in-app defenses that detect tampering, hooking, emulators and debuggers at runtime to prevent fraud and reverse engineering RASPIRE.
- UEBA and Behavioral Biometrics: continuous profiling of user and device behavior to surface anomalies that traditional controls miss.
- Mobile EDR / MTD integration with UEM: endpoint detection and response capabilities tailored for mobile telemetry, enabling automated remediation workflows within device management consoles.
- CI/CD security and SBOM: automated SAST/DAST, supply-chain vetting and continuous testing integrated into DevSecOps pipelines for mobile apps.
- Post-quantum and advanced cryptography: early adoption in secure communications and payment stacks to future-proof critical data.
- Cloud-native analytics and threat feeds: centralized threat intelligence and real-time analytics to scale detection across millions of devices Grand View Research – Mobile Security Market Size.
Mobile Device Security Funding
A total of 187 Mobile Device Security companies have received funding.
Overall, Mobile Device Security companies have raised $18.8B.
Companies within the Mobile Device Security domain have secured capital from 634 funding rounds.
The chart shows the funding trendline of Mobile Device Security companies over the last 5 years
Mobile Device Security Companies
- Protectt.ai — Protectt.ai offers AI-driven runtime protection and real-time fraud controls for mobile apps and devices, positioning its products as plug-in protections for enterprise mobile fleets and payment flows. The company advertises large session coverage targets and a combined mobile app/device protection suite emphasizing runtime self-protection and transaction fraud mitigation.
- Symmetrium — Symmetrium delivers a zero-trust mobile data governance platform that presents a native, streamed enterprise workspace to mobile users so sensitive data never sits on the endpoint. Their approach eliminates data-at-rest risk and targets enterprises that must limit data exfiltration while enabling remote collaboration.
- XFA — XFA provides device verification and compliance checks at sign-in without requiring full device control, enabling risk-based access decisions while preserving user privacy. The product fits organizations that need to enforce device posture for access but prefer agentless or low-friction deployment models.
- SaferCore — SaferCore markets a no-code, SaaS mobile app hardening and runtime protection stack that detects rooted/jailbroken devices, anti-debugging attacks and overlay threats. The company targets app owners seeking fast shielding without SDK complexity and focuses on blocking fraud mechanisms used against fintech and payment apps.
- Traced Mobile Security — Traced provides consumer and small business MTD with a focus on privacy-preserving telemetry and clear, actionable alerts for admins. Their Trustd platform combines a lightweight end-user app with enterprise dashboards for visibility into malicious apps, phishing and device compromise.
Enhance your understanding of market leadership and innovation patterns in your business domain.
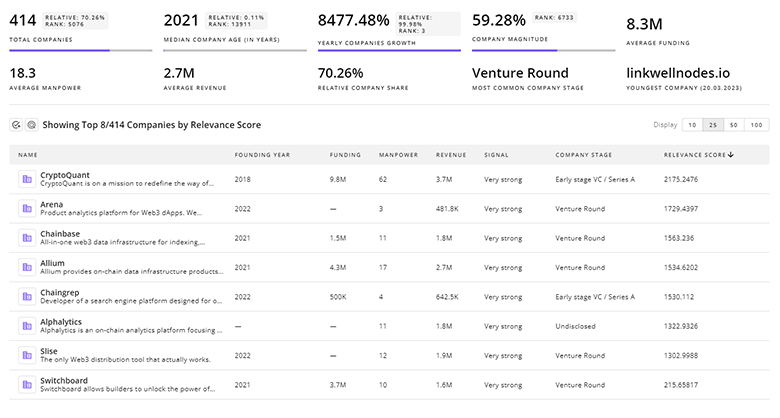
2.5K Mobile Device Security Companies
Discover Mobile Device Security Companies, their Funding, Manpower, Revenues, Stages, and much more
Mobile Device Security Investors
TrendFeedr’s Investors tool offers comprehensive insights into 657 Mobile Device Security investors by examining funding patterns and investment trends. This enables you to strategize effectively and identify opportunities in the Mobile Device Security sector.
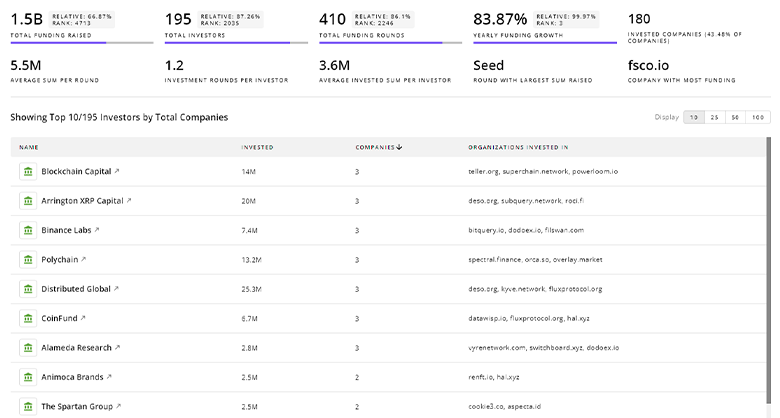
657 Mobile Device Security Investors
Discover Mobile Device Security Investors, Funding Rounds, Invested Amounts, and Funding Growth
Mobile Device Security News
TrendFeedr’s News feature provides access to 6.1K Mobile Device Security articles. This extensive database covers both historical and recent developments, enabling innovators and leaders to stay informed.
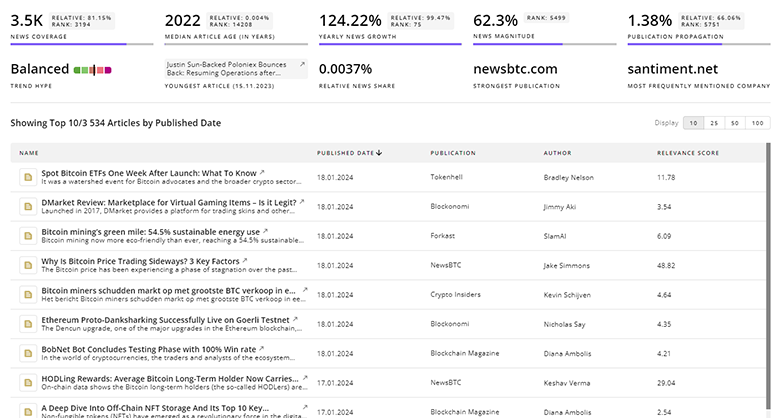
6.1K Mobile Device Security News Articles
Discover Latest Mobile Device Security Articles, News Magnitude, Publication Propagation, Yearly Growth, and Strongest Publications
Executive Summary
Mobile device security now sits at the intersection of device management, app supply-chain hygiene, identity controls and network protection. The market prizes solutions that deliver continuous device posture, AI-based anomaly detection, and friction-controlled access decisions that respect privacy and regulatory limits. Enterprises should prioritize architectures that integrate MDM/UEM, MTD and application protection into a single operating model so they can automate threat detection, reduce remediation time, and demonstrate compliance. Vendors that combine hardware trust anchors, runtime app protections and cloud analytics will widen competitive moats and meet the needs of regulated verticals where data sovereignty and high assurance matter.
We value collaboration with industry professionals to offer even better insights. Interested in contributing? Get in touch!