Smart Security Report
: Analysis on the Market, Trends, and TechnologiesThe smart security market is on track to expand from USD 132.94 billion in 2024 to USD 411.14 billion by 2034 at a CAGR of 11.95% (marketresearchfuture u2013 2025). This growth contrasts with a decline in news coverage of u201350.21% over the past five years, even as the topic maintains medium prevalence and involves 2,572 companies worldwide.
166 days ago, we last updated this report. Notice something that’s not right? Let’s fix it together.
Topic Dominance Index of Smart Security
To gauge the influence of Smart Security within the technological landscape, the Dominance Index analyzes trends from published articles, newly established companies, and global search activity
Key Activities and Applications
- Component Integration, Cloud Deployment, and Identity Management: Security systems now combine sensors, detectors, cameras, locks, access control, software, and services into unified platforms; cloud-based deployments generated USD 123.24 billion in revenues in 2024; biometric and passwordless methods such as FIDO passkeys are gaining adoption.
- Video Surveillance Systems: Networked cameras, recorders, and edge processors represented 46% of the smart home security services market in 2024, underlining video analytics as a dominant application (Smart Home Security Services Market Size, Scope, Forecast 2025).
- AI-Driven Threat Detection: Organizations deploy machine learning and AI models for real-time threat analytics and automated response, reducing detection times and false positives (Security Solutions Market Size u2013 Industry Analysis Report).
Emergent Trends and Core Insights
- AI and IoT Convergence: The integration of artificial intelligence with connected sensors and devices accelerates predictive analytics and situational awareness in both residential and commercial settings.
- Zero Trust Architecture Adoption: “Never trust, always verify” models are reshaping network and device security, driving micro-segmentation and continuous verification.
- Security Verification Seals: Initiatives like the Product Security Verified Mark provide consumers with a clear indication of device compliance with international cybersecurity standards (ZDNet).
- SMB-Focused Platforms: Unified security suites tailored for small and medium businesses simplify deployment and management, addressing resource constraints (BusinessWire).
Technologies and Methodologies
- Artificial Intelligence and Machine Learning: Core to threat identification, behavioral analytics, and automated policy adjustments.
- Internet of Things (IoT) Security: Protecting the network of interconnected devices to ensure data integrity and device authentication.
- Cloud Computing: Enables centralized data processing, storage, and analytics for scalable security operations.
- Biometric Authentication: Facial recognition, fingerprint scanning, and other biometric factors enhance access control and reduce reliance on passwords
- On-Device and Edge Processing: Performing critical security functions locally on cameras or workstations reduces latency and limits data exposure.
Smart Security Funding
A total of 259 Smart Security companies have received funding.
Overall, Smart Security companies have raised $11.3B.
Companies within the Smart Security domain have secured capital from 736 funding rounds.
The chart shows the funding trendline of Smart Security companies over the last 5 years
Smart Security Companies
- Secury360: Belgium-based provider of edge-and-cloud AI video analytics, Secury360 retrofits existing camera networks to deliver real-time intrusion prevention with minimal false alerts. Their plug-and-play box integrates seamlessly with leading VMS platforms, serving sectors from logistics hubs to construction yards.
- IntelliSee: Leveraging AI developed for defense applications, IntelliSee overlays live feeds to detect threatsu2014from active shooters to slip hazardsu2014and issues validated, location-specific alerts to security teams and integrations.
- Sentry AI: Sentry AI offers an “AI Guard for every site,” deploying computer-vision models to monitor cameras and dispatch verified alertsu2014helping security firms prevent crime, reduce penalties, and optimize staffing costs.
- MagicMirror Security: Developer of browser-embedded small language models for on-device data classification and policy enforcement, MagicMirror delivers real-time observability and controls without routing sensitive data to external servers.
Get detailed analytics and profiles on 3.0K companies driving change in Smart Security, enabling you to make informed strategic decisions.
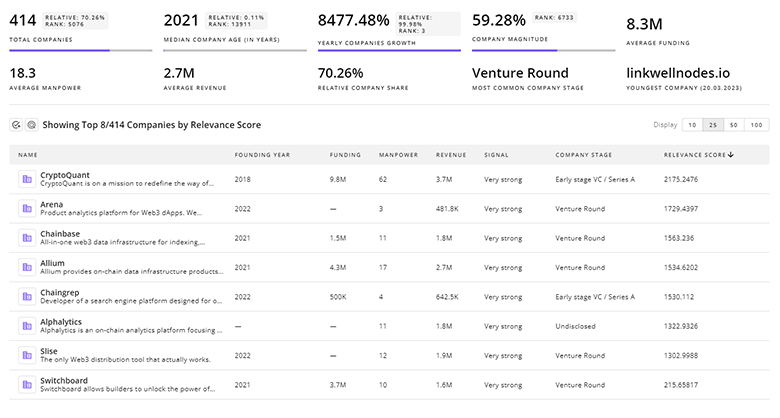
3.0K Smart Security Companies
Discover Smart Security Companies, their Funding, Manpower, Revenues, Stages, and much more
Smart Security Investors
TrendFeedr’s Investors tool provides an extensive overview of 813 Smart Security investors and their activities. By analyzing funding rounds and market trends, this tool equips you with the knowledge to make strategic investment decisions in the Smart Security sector.
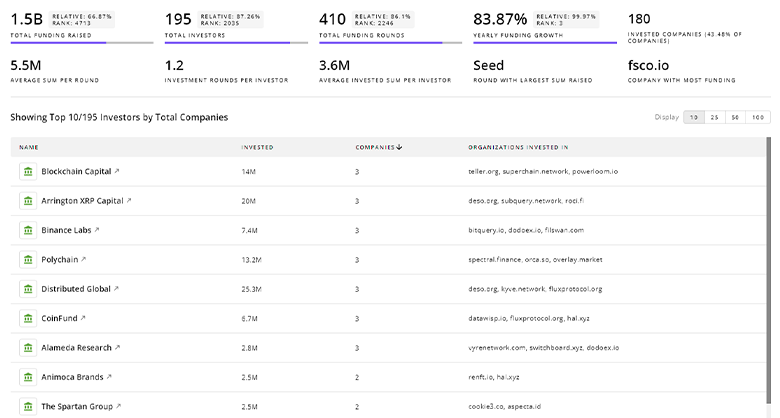
813 Smart Security Investors
Discover Smart Security Investors, Funding Rounds, Invested Amounts, and Funding Growth
Smart Security News
Explore the evolution and current state of Smart Security with TrendFeedr’s News feature. Access 4.6K Smart Security articles that provide comprehensive insights into market trends and technological advancements.
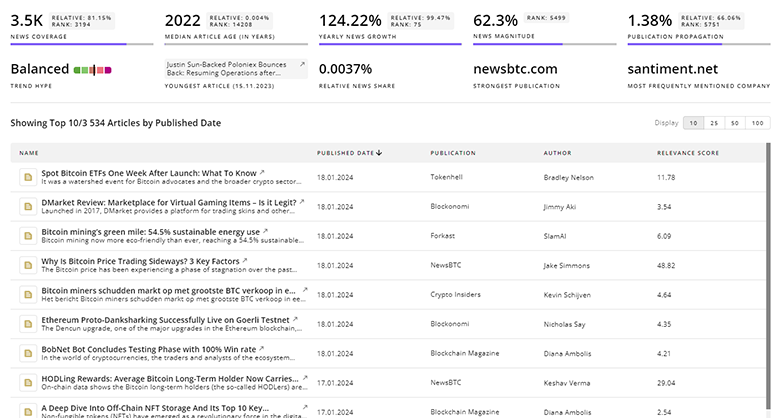
4.6K Smart Security News Articles
Discover Latest Smart Security Articles, News Magnitude, Publication Propagation, Yearly Growth, and Strongest Publications
Executive Summary
Smart security is evolving into an integrated ecosystem where AI, IoT, and cloud technologies converge to deliver predictive risk detection, streamlined management, and scalable deployments. Video analytics remains a cornerstone application, while edge-and-device computing reduces latency and enhances privacy. The ascent of Zero Trust models and security verification marks highlights a growing emphasis on continuous validation and regulatory compliance. For vendors, success will depend on packaging these capabilities into platforms that serve both enterprise-grade use cases and the resource constraints of SMBs, all while maintaining clear data privacy safeguards.
We're looking to collaborate with knowledgeable insiders to enhance our analysis of trends and tech. Join us!