Threat Modeling Report
: Analysis on the Market, Trends, and TechnologiesThe threat-modeling market is reaching operational scale: the market was $886,600,000 in 2022, with projected compound growth at 14.6% and a $3,400,000,000 market projection by 2032. The discipline is moving from one-off design exercises toward continuous, developer-centric programs that combine AI/ML for automated enumeration, attack emulation for validation, and business-context scoring to prioritize mitigations; this shift is driven by widespread SDLC integration, early evidence of AI-assisted adoption, and rising demand from cloud, IoT, and regulated verticals.
24 days ago, we last updated this report. Notice something that’s not right? Let’s fix it together.
Topic Dominance Index of Threat Modeling
To gauge the influence of Threat Modeling within the technological landscape, the Dominance Index analyzes trends from published articles, newly established companies, and global search activity
Key Activities and Applications
- SDLC integration and shift-left security: Embedding structured modeling at design, review, and pre-release gates to convert threats into actionable security requirements How Threat Modeling Enables Security by Design.
- Automated threat enumeration and prioritization using AI/ML: Applying LLMs and supervised ML to parse architectures, IaC, and code to produce prioritized threat lists and mitigation tasks.
- Continuous validation via BAS and simulation: Running continuous Breach and Attack Emulation to test whether modeled mitigations actually stop plausible TTPs and to measure residual risk.
- Threat-informed defense and control-effectiveness metrics: Mapping controls to adversary TTPs (MITRE ATT&CK) and converting threat models into measurable detection and response KPIs.
- AI model and agentic system threat modeling: Modeling prompt injection, data poisoning, model exfiltration, and governance controls for LLMs and multi-model pipelines.
- Human-factor and social engineering modeling: Simulating deepfake and spear-phishing attack paths to quantify organizational exposure and train human controls Breacher.ai.
- OT and critical-infrastructure path analysis: Mapping physical and cyber interactions to predict lateral movement in industrial networks and to prioritize firmware/patch programs OTraze.
Emergent Trends and Core Insights
- Widespread SDLC adoption and automation: Community data finds broad SDLC embedding; organizations that automate modeling reduce time to discovery and increase remediation throughput, making modeling part of delivery pipelines rather than an isolated security task State Of Threat Modeling 2025-2026.
- AI-assisted modeling with mixed strategic uptake: Roughly 48% of surveyed teams report use of AI-assisted tools, while only 22% apply disciplined future-back scenario planning—revealing a gap between tactical AI use and strategic foresight.
- LLM and knowledge-graph analytics tighten validation: Early adopters of knowledge graphs and LLM-driven enrichment report up to 40% reductions in false positives during model validation, enabling more precise threat prioritization.
- From architecture-centric to actor/behavioral modeling: Patent and research signals show a decisive move toward behaviorally informed models that profile threat actors and adjust baseline assumptions dynamically, as opposed to static DFD-only approaches.
- Sector specialization: BFSI, healthcare, and critical infrastructure demand domain-tailored modeling (privacy, regulatory auditability, safety integration), increasing the value of platforms that produce compliance artifacts automatically.
- Operationalization pressure: Vendors and R&D focus is now on translating model outputs into executable policies and CI/CD guardrails so that model findings produce immediate, measurable defensive action.
Technologies and Methodologies
- STRIDE, PASTA, LINDDUN and attack trees: Core structured taxonomies remain primary inputs for automated engines that generate threat hypotheses and requirements Threat Modeling - OWASP Cheat Sheet Series.
- LLM-assisted hypothesis generation and risk reasoning: LLMs automate threat enumeration from design docs, generate test cases, and draft mitigation playbooks while requiring supervised validation for accuracy Proactive Cybersecurity Defense Through Future-Back ….
- Knowledge graphs for contextual correlation: Graph platforms link assets, identities, vulnerabilities, and external CTI to compute contextualized risk scores and attack paths, improving prioritization precision Threat Intelligence Analytics Trends.
- Breach and Attack Simulation (BAS) and continuous red/ purple teaming: Automated adversary emulation validates modeled mitigations and measures real-world control efficacy on an ongoing basis Attack Simulation Proactive Market Research Report.
- Security Chaos Engineering (SCE): Injecting controlled failures and attack scenarios into production to validate resilience assumptions derived from threat models.
- IaC and runtime model extraction: Tools that derive models directly from Infrastructure as Code and runtime telemetry reduce manual DFD creation and keep models synchronized with ephemeral cloud states ThreatModeler v7.2 announcement.
- Risk quantification frameworks integrating CVSS + financial impact: Combining vulnerability severity with business impact metrics produces prioritized remediation roadmaps that are defensible to finance and executive stakeholders Threat Modeling Tools Market.
Threat Modeling Funding
A total of 83 Threat Modeling companies have received funding.
Overall, Threat Modeling companies have raised $3.3B.
Companies within the Threat Modeling domain have secured capital from 298 funding rounds.
The chart shows the funding trendline of Threat Modeling companies over the last 5 years
Threat Modeling Companies
- DevArmor — DevArmor automates security reviews and threat modeling with developer workflow integrations (Jira, GitHub, Terraform) to generate structured model outputs and enforcement checks. The platform claims it can reduce security backlog by 80% and save security teams 30% of their time while accelerating releases by three months, positioning the product as a gatekeeper that keeps velocity high without sacrificing design-time security.
- Heeler — Heeler focuses on open-source risk remediation by combining static and runtime analysis with embedded runtime threat modeling to surface what is actually exploitable in a codebase and to generate validated pull requests for fixes, reducing developer triage overhead and prioritizing remediation that matters to runtime exposure.
- RedMimicry GmbH — RedMimicry provides automated breach and attack emulation optimized for consulting and purple-team engagements, delivering continuously updated malware emulation scenarios that mirror real actor TTPs so customers can validate detection pipelines and response playbooks against current threats.
- Ailtire — Ailtire builds business-aware, automated threat modeling aimed at product teams; the tool converts design inputs into control mappings and risk scores, prioritizing changes that align with business objectives and compliance requirements—helpful for teams that need lightweight, rapid modeling without heavy process overhead.
Get detailed analytics and profiles on 809 companies driving change in Threat Modeling, enabling you to make informed strategic decisions.
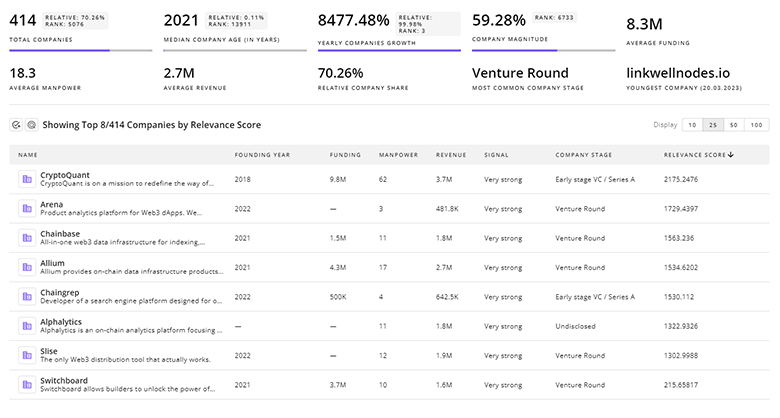
809 Threat Modeling Companies
Discover Threat Modeling Companies, their Funding, Manpower, Revenues, Stages, and much more
Threat Modeling Investors
TrendFeedr’s Investors tool provides an extensive overview of 455 Threat Modeling investors and their activities. By analyzing funding rounds and market trends, this tool equips you with the knowledge to make strategic investment decisions in the Threat Modeling sector.
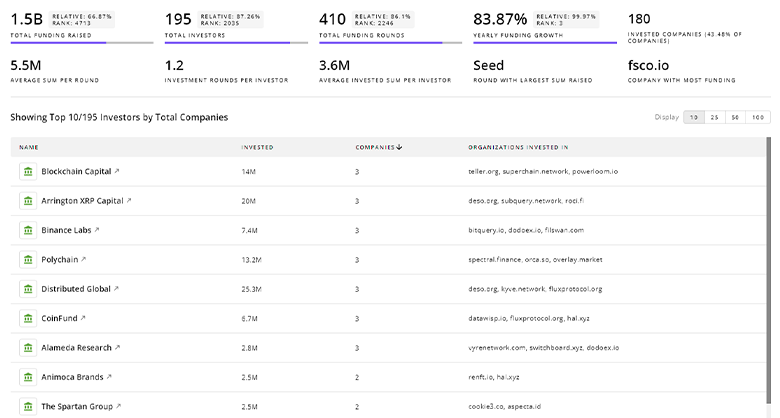
455 Threat Modeling Investors
Discover Threat Modeling Investors, Funding Rounds, Invested Amounts, and Funding Growth
Threat Modeling News
Explore the evolution and current state of Threat Modeling with TrendFeedr’s News feature. Access 562 Threat Modeling articles that provide comprehensive insights into market trends and technological advancements.
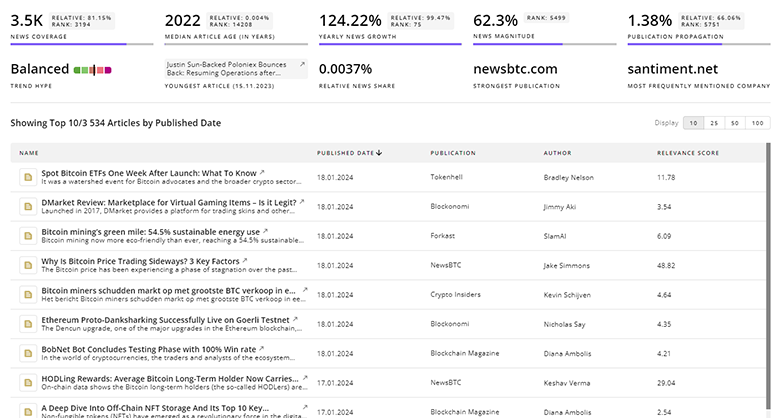
562 Threat Modeling News Articles
Discover Latest Threat Modeling Articles, News Magnitude, Publication Propagation, Yearly Growth, and Strongest Publications
Executive Summary
Threat modeling now matters where software and systems change fastest: in CI/CD pipelines, cloud runtimes, LLM deployments, and industrial control systems. Organizations will derive measurable defensive value by turning models into continuous validation programs that (1) feed attack emulation and detection engineering, (2) produce prioritized, business-mapped remediation actions, and (3) instrument model outputs as policy artifacts in developer workflows. For security leaders, the priority is pragmatic: adopt tooling that integrates with delivery pipelines, require multidisciplinary modeling sessions to raise identification rates, and invest in targeted automation (knowledge graphs, LLM assistance, BAS) to reduce noise while increasing the fidelity of prioritized mitigations.
We're looking to collaborate with knowledgeable insiders to enhance our analysis of trends and tech. Join us!