Cybersecurity Report
: Analysis on the Market, Trends, and TechnologiesThe global cybersecurity market sits at a meaningful inflection point: the internal trend data puts 2024 market size at USD 199.0 billion and projects USD 301.4 billion by 2030 (CAGR 7.2%), signaling sustained commercial demand for managed security, cloud posture controls, and identity protections Cybersecurity Industry Outlook 2024. This growth reflects three forces converging: increasing cloud and IoT footprints that expand attack surfaces, the rapid adoption of AI by attackers and defenders, and rising regulatory and insurance-driven spending that pushes organizations toward outcome-based, managed security models Top Cybersecurity Statistics: Facts, Stats and Breaches for 2025.
We updated this report 116 days ago. Noticed something’s off? Let’s make it right together — reach out!
Topic Dominance Index of Cybersecurity
The Topic Dominance Index trendline combines the share of voice distributions of Cybersecurity from 3 data sources: published articles, founded companies, and global search
Key Activities and Applications
- Managed Detection & Response (MDR) and SOC-as-a-Service — continuous monitoring, threat hunting, and 24x7 incident response remain the primary operational demand from enterprises and SMBs; outsourcing reduces internal staffing pressure and shortens time-to-containment
So what: Organizations lacking skilled analysts convert fixed-headcount risk into variable, service-priced resilience. - Identity & Access Management (IAM) and Zero Trust implementations — identity controls, ZTNA, and least-privilege enforcement are now core parts of architecture workstreams as credentials and identity-based attacks dominate initial access.
So what: IAM becomes the first line of risk reduction for cloud and hybrid estates; maturity here materially shrinks blast radius. - Cloud Security Posture Management (CSPM) and CNAPP — continuous posture, misconfiguration detection, and cloud workload protection address the fastest-growing exposure as workloads migrate to multi-cloud Cloud Intrusion Protection Software Market.
So what: Continuous posture automation transforms compliance budgets into operational security value. - Vulnerability Management, Continuous Penetration Testing, and Supply-chain Security — automated scanning plus expert red-team validation meets the rise in software/API exploited as initial access vectors Top Enterprise Cybersecurity Shortcomings, 2023.
So what: Prioritization (risk-based remediation) determines whether vulnerability investments reduce real exposure. - Human risk reduction and security skills development — awareness programs, phishing simulations, and cyber skilling address the continuing role of human error in breaches News Landscape Report: The Human Side of Cybersecurity.
So what: Measured improvement in staff behavior reduces incident likelihood and supports faster detection.
Emergent Trends and Core Insights
- AI arms race: attackers use generative models for phishing and automation while defenders embed ML for detection, triage, and automated playbooks; this dual use forces security teams to combine ML with human oversight to avoid detection gaps Cybersecurity market — forward-looking insight & prediction (2025-2045) Zero Trust: Strengths and Limitations in the AI Attack Era.
So what: Investment must cover both ML models and the operational processes that validate them. - Platform consolidation and managed outcomes: buyers prefer integrated XDR/XSOAR/CNAPP stacks or managed providers that deliver SLAs and measurable risk reduction, accelerating MSSP/MDR adoption Cybereason.
So what: Niche point products must either embed into platforms or concentrate on highly specialized, non-commoditized capabilities. - Risk quantification and insurance coupling: cyber-insurance growth and regulatory pressure push organizations to quantify cyber financial exposure and to buy controls that demonstrably lower premiums Cyber-Resilience — Turning Every Crisis into an Opportunity to Emerge Stronger.
So what: Security tooling that produces auditable, insurer-grade evidence gains commercial advantage. - Cloud/IOT/OT convergence increases attack surface: multi-cloud and IIoT create cross-domain risks and demand vendor-agnostic asset visibility and segmentation Cloud Security Posture Management.
So what: Asset discovery and continuous segmentation become priority projects to reduce systemic risk. - Skills and tooling interoperability problems persist: organizations juggle many tools and face integration overhead; standardization and SOAR/XDR integration increase defender speed Cybersecurity and the Problem of Interoperability.
So what: Investment in orchestration and telemetry pipelines yields outsized operational gains.
Technologies and Methodologies
- AI / ML for detection, triage, and predictive analytics — used across XDR, CSPM, and threat intelligence to reduce dwell time and prioritize response.
So what: Teams must balance model performance, explainability, and operational validation to avoid blind spots. - Zero Trust Architecture (ZTNA) and identity-centric controls — continuous verification and least privilege replace perimeter assumptions as remote work and SaaS use grow.
So what: ZTNA drives IAM, device posture, and microsegmentation projects. - XDR, SOAR, and automated incident orchestration — toolchains that correlate telemetry and automate playbooks reduce manual toil and improve time-to-remediate.
So what: Orchestration platforms scale scarce analyst capacity into faster containment. - CNAPP / CSPM / CWPP convergence for cloud security — unified cloud posture and workload protections address multi-cloud complexity and supply-chain misconfigurations.
So what: End-to-end cloud security stacks reduce point-product fragmentation and audit friction. - Security-as-Code, DevSecOps and shift-left testing — automated SAST/DAST/SCA and policy-as-code embed security earlier in SDLC to reduce post-deployment exposure Embracing Security Code.
So what: Shifting remediation upstream lowers the total cost of vulnerability management. - Behavioral analytics, deception tech, and cyber ranges — user/entity behavior analytics (UEBA), adaptive honeypots, and skills platforms raise detection fidelity and human readiness Cyberbit.
So what: Combining simulation-based training with telemetry testing hardens both people and processes.
Cybersecurity Funding
A total of 22.0K Cybersecurity companies have received funding.
Overall, Cybersecurity companies have raised $2.3T.
Companies within the Cybersecurity domain have secured capital from 74.8K funding rounds.
The chart shows the funding trendline of Cybersecurity companies over the last 5 years
Cybersecurity Companies
- CyberSecOp — CyberSecOp offers SOC-as-a-Service, managed SIEM, MDR, and vCISO/compliance advisory that help regulated firms close audit gaps and operationalize detection and response. The firm emphasizes compliance-driven SOC workflows and rapid incident response, making it a practical option for midsize firms that cannot staff a full in-house SOC. Its service mix aligns with the market shift toward managed outcomes and evidence-based compliance.
- cyberSecurist Technologies — A specialist in application and product security, this firm focuses on VAPT, secure deployment assurance, and developer-centric remediation services for software vendors and enterprises. Its approach addresses the persistent application and API weaknesses that studies show drive a growing share of breaches.
- CyberSquare — CyberSquare provides targeted ethical-hacking, pentesting, and a bespoke framework for detecting data leaks across web and social channels. The company couples offensive testing with rapid advisory remediation, a fit for customers who need focused, high-skill validation rather than broad platform coverage.
- Computed Future — A small firm that builds predictive security models trained on attack paths and runtime signals, Computed Future aims to identify malicious intent earlier in cloud and endpoint workloads. Its predictive emphasis matches the emergent trend toward proactive detection and risk quantification while remaining lightweight for integration into larger telemetry pipelines.
- Cyber Sierra — Cyber Sierra combines continuous control monitoring, third-party risk management, and GRC workflows into a platform tailored for rapidly scaling enterprises. The firm links control evidence to compliance reporting and insurance readiness, addressing insurers' rising demand for auditable control telemetry.
Gain a better understanding of 324.0K companies that drive Cybersecurity, how mature and well-funded these companies are.
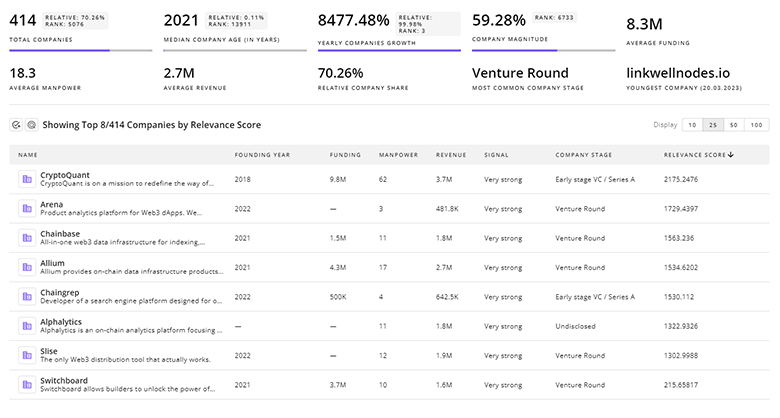
324.0K Cybersecurity Companies
Discover Cybersecurity Companies, their Funding, Manpower, Revenues, Stages, and much more
Cybersecurity Investors
Gain insights into 47.4K Cybersecurity investors and investment deals. TrendFeedr’s investors tool presents an overview of investment trends and activities, helping create better investment strategies and partnerships.
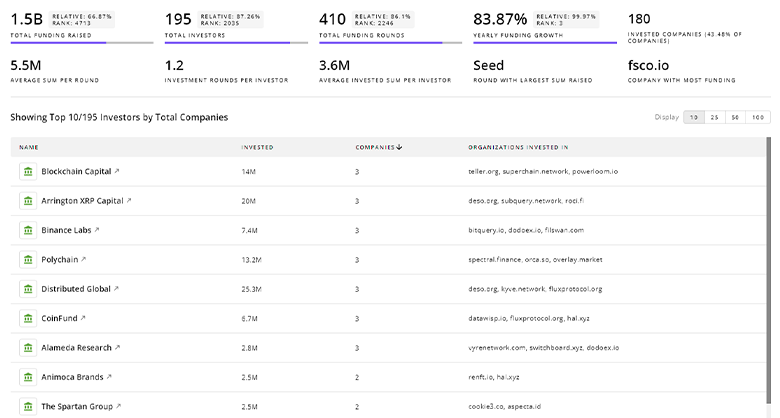
47.4K Cybersecurity Investors
Discover Cybersecurity Investors, Funding Rounds, Invested Amounts, and Funding Growth
Cybersecurity News
Gain a competitive advantage with access to 414.6K Cybersecurity articles with TrendFeedr's News feature. The tool offers an extensive database of articles covering recent trends and past events in Cybersecurity. This enables innovators and market leaders to make well-informed fact-based decisions.
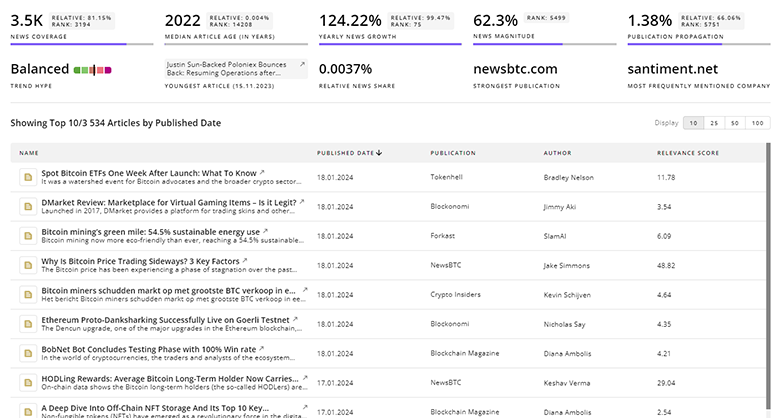
414.6K Cybersecurity News Articles
Discover Latest Cybersecurity Articles, News Magnitude, Publication Propagation, Yearly Growth, and Strongest Publications
Executive Summary
The data indicates a market that rewards measurable security outcomes: continuous monitoring, identity-first architectures, cloud posture automation, and AI-augmented detection form the commercial center. Security leaders should convert security investments into auditable reductions in business risk by prioritizing identity controls, cloud posture automation, and managed detection capabilities. Vendors that provide clear, insurer-grade evidence of control effectiveness or that integrate as indispensable components of larger, telemetry-driven platforms will capture accelerating share. Finally, organizations that combine tool consolidation, orchestration, and ongoing skills validation will reduce dwell time and cost per incident, turning cybersecurity from a compliance cost into a manageable operational risk control.
We seek partnerships with industry experts to deliver actionable insights into trends and tech. Interested? Let us know!