Edge Security Report
: Analysis on the Market, Trends, and TechnologiesThe edge security market has reached a turning point: estimated at $30,700,000,000 in 2024 with a reported compound annual growth rate of 21.2%, the sector is forecast to rise to $97,100,000,000 by 2030, signaling large-scale commercial opportunity for solutions that secure compute and data where they originate. Market forecasts and vendor activity show two simultaneous dynamics: (1) rapid expansion of cloud-native access and threat-analytics stacks tied to mobile, 5G, and edge AI deployments Global Edge Security Market: Trends and Forecast (2023-2028) and (2) continued demand for hardware-anchored isolation and one-way controls for industrial and critical-infrastructure use cases. Those twin forces favor vendors that can pair low-latency, on-device detection with hardware-rooted attestation and identity-centric access controls, and they create windows for niche specialists to capture high-value contracts in regulated industries.
This article was last updated 8 days ago. If you find any info is missing, let us know!
Topic Dominance Index of Edge Security
The Dominance Index of Edge Security looks at the evolution of the sector through a combination of multiple data sources. We analyze the distribution of news articles that mention Edge Security, the timeline of newly founded companies working in this sector, and the share of voice within the global search data
Key Activities and Applications
- Real-time, on-device threat detection and response. Deploying lightweight AI/ML models on gateways, routers, and constrained IoT endpoints to detect anomalies and trigger immediate local remediation reduces dependence on backhaul to central SOCs and addresses intermittent connectivity in field deployments.
- Zero-trust access and identity-driven microsegmentation. Enforcing identity and attribute-based policies at the edge (ZTNA/ZT Architecture) to limit lateral movement across IT/OT/IoT domains and support least-privilege access for ephemeral workloads.
- Hardware-enforced one-way data flows and air-gap controllers. Physical isolation appliances and unidirectional gateways protect critical OT and industrial telemetry while preserving supervisory visibility and data ingestion for analytics.
- Edge SASE and distributed Secure Web Gateway (SWG) deployments. Extending SASE/SSE capabilities to distributed POPs and MEC nodes to consolidate SWG, CASB, and firewall functions close to users and devices reduces latency and preserves security posture at the network edge.
- Firmware and embedded-software protection for IP-sensitive devices. Techniques that prevent reverse engineering and secure firmware update pipelines protect product IP and limit supply-chain exposure for connected devices in automotive, medical, and industrial sectors.
- External attack surface and shadow-API discovery for distributed systems. Continuous discovery of internet-exposed and shadow assets that bypass centralized gateways prevents blind spots that adversaries exploit in hybrid, service-mesh, and direct workload-to-workload API calls Gaps in API-centric protection.
- Managed detection and response (MDR) tailored to edge topologies. MDR and cloud-based orchestration that combine local enforcement with centralized analytics meet availability and compliance needs for customers lacking in-house edge security expertise.
Emergent Trends and Core Insights
- Hardware-anchored trust is moving from niche to standard for high-risk deployments. There is rising patent and product activity around hardware roots of trust, secure enclaves, and FPGA-based isolation intended to create tamper-resistant security primitives at the point of data collection.
- Edge and SASE integration accelerates vendor consolidation. Vendors that combine Secure Access Service Edge with edge compute orchestration win enterprise deals because they lower management overhead and reduce the number of control planes an operator must manage Edge Security Market – Worldwide | Future Scope & Trends.
- Regulation is shaping architecture choices. Data-sovereignty and privacy laws push processing to local nodes and favor solutions that provide provable locality, encrypted enclaves, and selective reporting to central systems.
- AI at the edge is a double-edged accelerator. On-device models enable high-fidelity detection with low latency, but they also increase the attack surface and demand secure model provisioning, verification, and federated updating practices.
- Operational and human-factor vectors remain primary risk drivers. Nonlocal maintenance, third-party remote sessions, and insider amplification of attacks require session control, ephemeral credentials, and contextual ML to spot atypical human behavior before exfiltration Egress, a KnowBe4 company.
- Specialists win in verticals where physical exposure and continuity matter. Energy, water, transportation, and defense prefer hardware-anchored isolation and one-way controls; commercial IT favors cloud-centric SASE stacks. This bifurcation creates parallel procurement tracks and tailored risk models.
Technologies and Methodologies
- Zero Trust Network Access (ZTNA) and IdentityGraph microsegmentation. Identity-centric segmentation that maps device, user, and application attributes to dynamic policies minimizes lateral risk and simplifies compliance controls for distributed assets Elisity.
- Hardware roots of trust, secure enclaves, and FPGA-based isolation. Enforced at silicon or FPGA level to provide immutable attestation and one-way data flows for OT and high-assurance edge nodes Q-Net Security.
- On-device ML inference and federated learning. Lightweight model compression and federated update methods enable pattern recognition without exporting raw telemetry, preserving privacy and reducing bandwidth.
- Content Disarm and Reconstruction (CDR) at gateways. File-level sanitization eliminates weaponized content while preserving usability for workflows that require native formats, mitigating zero-day file attacks at ingestion points Resec.
- One-way diodes and physical air-gap controllers. Deterministic, hardware-only controls that allow telemetry to leave a site but prevent inbound compromise remain the strongest practical defense for many CNI deployments Fend Incorporated.
- Secure firmware lifecycle and supply-chain attestation. Signed updates, device fingerprinting, and policy-driven rollout orchestrations reduce risk from compromised third-party components and firmware tampering.
- Edge SASE stacks with local policy enforcement. Combining SD-WAN, SWG, CASB, and ZTNA into a distributed service that enforces policies at local POPs reduces hair-pinning and improves UX while maintaining centralized governance Edge Security Market to Reach $136,453.0 Million by 2034 Globally.
Edge Security Funding
A total of 157 Edge Security companies have received funding.
Overall, Edge Security companies have raised $6.8B.
Companies within the Edge Security domain have secured capital from 457 funding rounds.
The chart shows the funding trendline of Edge Security companies over the last 5 years
Edge Security Companies
SECeDGE
SECeDGE provides a digital security SaaS platform for IoT and Edge AI devices with device-level controls, zero-trust networking, and remote connectivity that can leverage on-demand cellular and broadband links. The company expanded capability through the acquisition of Sequitur Labs and closed a Series A that totaled $19.85M, highlighting investor belief in edge-native SaaS that secures the compute and control plane. SECeDGE targets industrial and enterprise customers that require device attestation, secure data management, and lifecycle control without heavy device reengineering.Terafence
Terafence markets a hardware-based unidirectional gateway that enforces physical segmentation by design: the appliance lacks IP, OS, and negotiable ports, eliminating conventional network attack surfaces and allowing safe telemetry outflow while preventing inbound compromise. The design suits high-assurance OT and critical infrastructure where software patches cannot provide acceptable guarantees. Enterprises with strict continuity requirements adopt this pattern to preserve supervisory control and analytics while isolating supervisory networks.emproof
emproof delivers firmware protection and IP integrity tools that prevent reverse engineering and exploitation of embedded code. The Nyx solution processes and hardens binaries, enabling security teams and OEMs to add protection late in the lifecycle without full source access. This approach appeals to automotive, industrial, and medical device manufacturers focused on preserving product IP and meeting rising regulatory expectations for secure device lifecycles.EdgeBit
EdgeBit automates dependency and supply-chain security by linking vulnerability analysis to runtime usage, helping engineering teams find and remediate only the dependencies that are actually active in production. The platform accelerates secure updates, reduces triage overhead, and shortens remediation cycles—capabilities that matter as distributed edge stacks multiply in complexity. For organizations shipping frequent edge software updates, this reduces security debt and improves incident response time.
Uncover actionable market insights on 2.4K companies driving Edge Security with TrendFeedr's Companies tool.
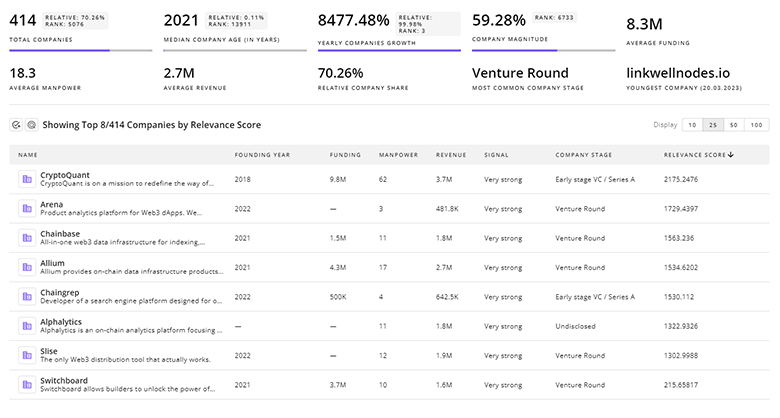
2.4K Edge Security Companies
Discover Edge Security Companies, their Funding, Manpower, Revenues, Stages, and much more
Edge Security Investors
Get ahead with your investment strategy with insights into 477 Edge Security investors. TrendFeedr’s investors tool is your go-to source for comprehensive analysis of investment activities and financial trends. The tool is tailored for navigating the investment world, offering insights for successful market positioning and partnerships within Edge Security.
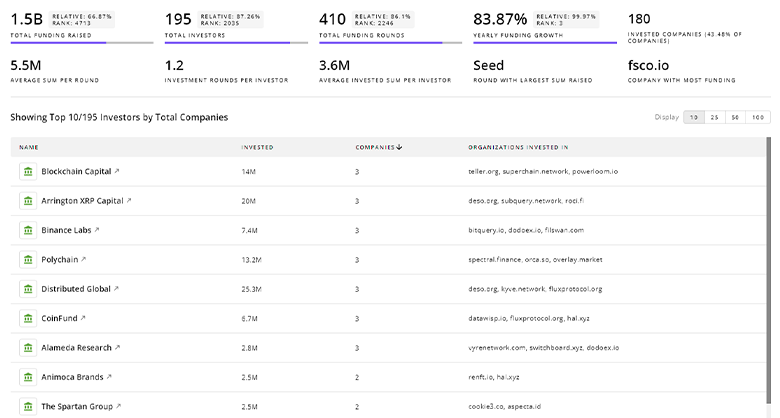
477 Edge Security Investors
Discover Edge Security Investors, Funding Rounds, Invested Amounts, and Funding Growth
Edge Security News
TrendFeedr’s News feature offers access to 1.5K news articles on Edge Security. The tool provides up-to-date news on trends, technologies, and companies, enabling effective trend and sentiment tracking.
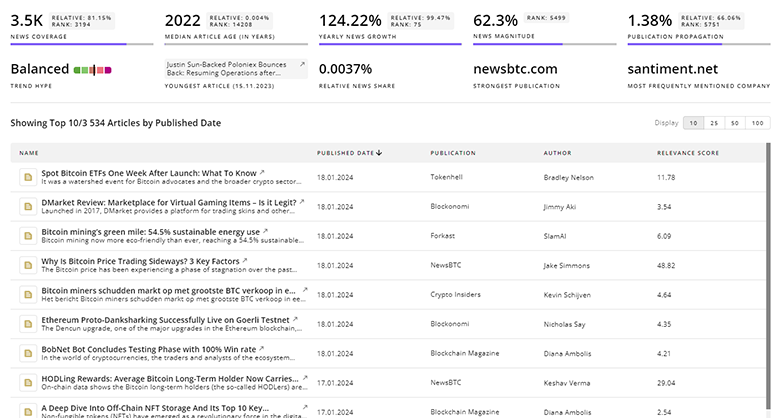
1.5K Edge Security News Articles
Discover Latest Edge Security Articles, News Magnitude, Publication Propagation, Yearly Growth, and Strongest Publications
Executive Summary
Edge security now requires parallel investment tracks: hardware-anchored isolation and attestation for industrial and high-assurance sites, and software-centric identity, policy, and ML stacks for distributed commercial workloads. Market sizing and forecasts indicate scale—$30.7B today expanding at roughly 21.2% CAGR—but they also reveal segmentation: buyers will select either hardened physical primitives or integrated SASE/ZTNA platforms depending on continuity, compliance, and latency needs. Strategic winners will integrate device-level trust with centralized policy orchestration, minimize operational friction for frontline teams, and offer clear proof points for data locality and attestation. Businesses should map edge risk to procurement categories (physical isolation, device hardening, access fabric, runtime analytics) and pursue partnerships that deliver verifiable hardware trust and identity-centric policy enforcement together.
Have expertise in trends or technology? Your input can enrich our content — consider collaborating with us!