Prompt Injection Defense Report
: Analysis on the Market, Trends, and TechnologiesThe prompt injection defense market reached USD 1.14 billion in 2024, reflecting high enterprise spend on mitigation as incidents rose sharply, with a u224835% increase in reported attacks and a 12% success rate against naive safety prompts, underlining immediate operational risk Prompt Injection Defense Market Research Report 2033 – Dataintelo. Rapid market growth (projected u224822% CAGR through 2033) is driving investment into layered, low-latency controls that protect retrieval-augmented generation pipelines, agentic workflows, and enterprise-facing LLM endpoints while automated adversarial testing and adaptive defenses begin to materially reduce exposure Defending AI Systems Against Prompt Injection Attacks – Wiz.
The last time we updated this report was yesterday. If there’s something missing or off, your tips are welcome!
Topic Dominance Index of Prompt Injection Defense
The Dominance Index for Prompt Injection Defense merges timelines of published articles, newly founded companies, and global search data to provide a comprehensive perspective into the topic.
Key Activities and Applications
- Input Validation & Sanitisation — Preprocessing stacks that normalise encodings, strip obfuscation (Base64, Unicode homoglyphs), and apply semantic intent filters before prompts reach the model. Practical deployments combine syntactic cleaning with semantic scoring to reduce false negatives LLM01:2025 Prompt Injection – OWASP Gen AI Security Project.
- Context Isolation and Delimiter Enforcement — Architectural separation of system prompts, tool-invocation tokens, and user data so instruction tokens remain privileged and immutable during inference. This pattern reduces direct overwrite attacks on system instructions and protects RAG sources.
- Runtime Behavioural Monitoring — Low-overhead telemetry and anomaly detection that flags unusual tool calls, token-generation pacing, or API access patterns in real time, enabling immediate containment of suspected injection events.
- Stored-Prompt and Data Provenance Scanning — Continuous scanning of knowledge bases, document stores, and training corpora to find persistent malicious instructions that can survive model updates and poison downstream RAG outputs.
- Automated Red-Team & Fuzzing Toolchains — Programmatic adversaries and RL-based attackers that discover subtle multi-turn injection chains and train detection rules; these tools inform both model tuning and guardrail policy updates Innovative Defenses Against Prompt Injection Attacks – arXiv.
- Policy Gateways and Validator Agents — Middleware that treats LLMs as untrusted components, validating outputs against policy rules and performing response-level sanitisation before downstream actions or disclosures occur Framework Achieves Multimodal Prompt Injection Attack Prevention in Agentic AI Systems.
Emergent Trends and Core Insights
- The market is shifting from single-filter prevention toward layered impact reduction, because major vendors and national cyber agencies now assess prompt injection as fundamentally persistent; security strategy is moving to limit consequences, not promise total elimination Prompt Injection Can’t Be Fully Mitigated, NCSC Says Reduce Impact Instead.
- Commercialisation is accelerating, with USD 1.14 billion market size and projected u224822% CAGR, producing a bifurcation between platform vendors offering end-to-end AI security stacks and small, high-leverage primitives that secure specific failure modes (RAG, agent orchestration, stored-prompt hygiene) Prompt Security.
- RAG pipelines represent the highest immediate business risk because indirect injections hide malicious instructions inside retrieved documents, turning ordinary knowledge sources into long-term poisoning vectors Indirect prompt injection attacks target common LLM data sources.
- Automated adversaries are discovering multi-turn escalation paths that human red teams miss; defenders increasingly use RL-crafted attack generators to keep detection policies current, with prototype systems reporting measurable lifts in detection of novel attacks (~18% improvement vs static rule sets in research prototypes).
- The enterprise adoption gap remains wide, with less than 35% of organizations deploying dedicated defenses, creating a large commercial runway for vendor solutions that combine low latency with governance and forensic logging OpenAI defensive posture reporting.
- There is notable convergence between client-side supply-chain protections and LLM defenses, since untrusted front-end content can weaponize prompts delivered to browser-embedded agents Source Defense client-side research.
Technologies and Methodologies
- Semantic Prompt Sanitiser — NLP models that score intent and flag instruction-like content even when heavily obfuscated, augmenting regex and rule systems What is a Prompt Injection Attack? – Trend Micro (UK).
- Contextual State Machines for LLM Pipelines — Strict, multi-state orchestration where inputs must pass defined checkpoints (schema validation, provenance check, intent score) before the model may access sensitive tool calls or APIs, mirroring mechanical interlock design patterns from safety engineering research.
- Runtime eBPF and Lightweight Telemetry — High-fidelity, low-cost process monitoring that detects anomalous system interactions and unusual call patterns linked to exfiltration attempts.
- Validator Agents and Output Firewalls — Secondary models or policy engines that vet LLM outputs before they are acted upon, implementing enforced least privilege and granular API gating for agentic workflows.
- Self-Invalidating Session Controls — Session-level cryptographic keys or context tokens that can be invalidated on high-confidence detection, effectively making a successful injection non-repeatable and limiting dwell time; conceptually parallel to single-use mechanical safety mechanisms in regulated hardware patents.
- Adversarial Continuous Testing — Automated attack generation pipelines that feed live discovered vectors back into model hardening and policy tuning, shortening the detection-to-remediation cycle.
Prompt Injection Defense Funding
A total of 86 Prompt Injection Defense companies have received funding.
Overall, Prompt Injection Defense companies have raised $3.7B.
Companies within the Prompt Injection Defense domain have secured capital from 265 funding rounds.
The chart shows the funding trendline of Prompt Injection Defense companies over the last 5 years
Prompt Injection Defense Companies
- Operant AI — Operant AI delivers a 3D Runtime Defense platform that targets runtime threats across APIs, containers, and LLMs with a single-step deployment model and low instrumentation overhead. The product emphasizes active blocking of data exfiltration and prompt injection attempts in high-throughput inference environments, aiming to preserve latency while enforcing policy. Operant reports $13.50M total funding and positions runtime firewalling as its core differentiator.
- Innoculator — Innoculator applies AI-driven virtual patching to legacy applications, providing agentless protection that prevents attackers from exploiting unpatched surfaces that can act as pivot points after an LLM compromise. The startup is intentionally small and research-focused, offering low-cost deployment options for enterprises that must secure aging stacks linked to LLM front ends.
- Heeler — Heeler focuses on application security posture management with AI-driven fixes and runtime threat modelling, closing the gap between code findings and safe production rollouts. For organizations embedding LLMs into products, Heeler’s agentic remediation and validated PR generation accelerate secure deployments and reduce developer friction; the company has raised $9.00M to scale this integration.
- Spyderbat — Spyderbat offers real-time cloud and Kubernetes detection built on low-level telemetry, enabling precise root-cause analysis and rapid containment of anomalous behaviour tied to injection attempts. The approach reduces investigation time and helps SOC teams surface subtle exfiltration patterns that often accompany successful prompt injections.
Delve into the corporate landscape of Prompt Injection Defense with TrendFeedr’s Companies tool
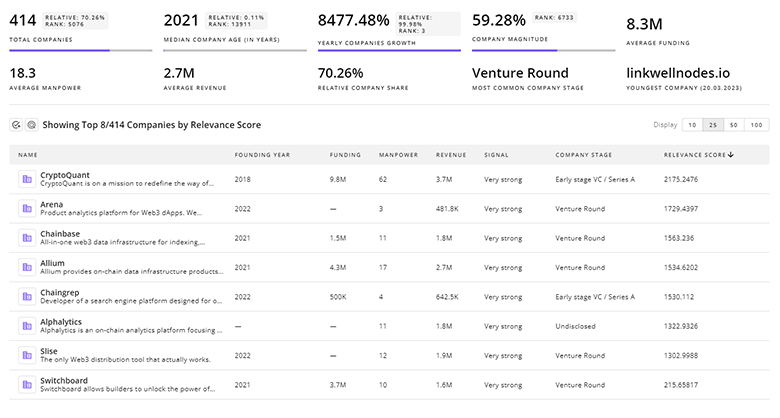
317 Prompt Injection Defense Companies
Discover Prompt Injection Defense Companies, their Funding, Manpower, Revenues, Stages, and much more
Prompt Injection Defense Investors
TrendFeedr’s Investors tool provides insights into 566 Prompt Injection Defense investors for you to keep ahead of the curve. This resource is critical for analyzing investment activities, funding trends, and market potential within the Prompt Injection Defense industry.
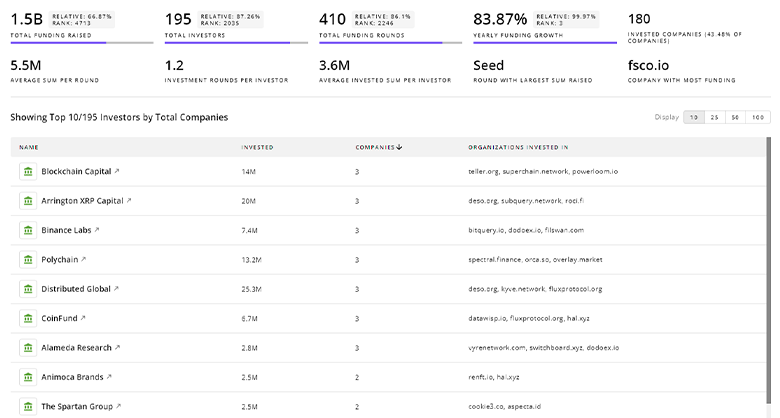
566 Prompt Injection Defense Investors
Discover Prompt Injection Defense Investors, Funding Rounds, Invested Amounts, and Funding Growth
Prompt Injection Defense News
TrendFeedr’s News feature offers you access to 1.1K articles on Prompt Injection Defense. Stay informed about the latest trends, technologies, and market shifts to enhance your strategic planning and decision-making.
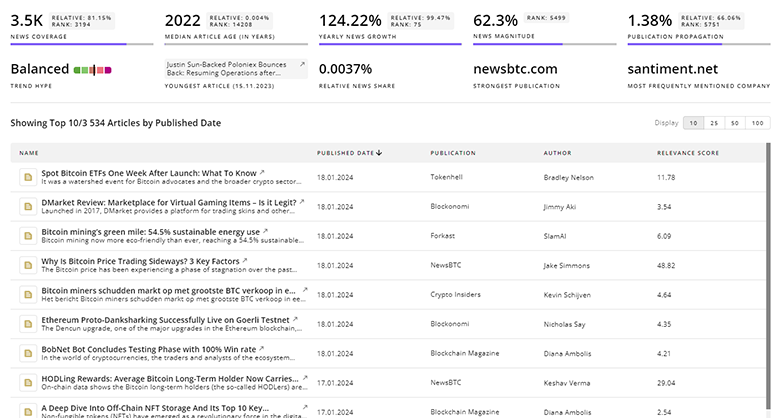
1.1K Prompt Injection Defense News Articles
Discover Latest Prompt Injection Defense Articles, News Magnitude, Publication Propagation, Yearly Growth, and Strongest Publications
Executive Summary
Prompt injection is now a measured, high-value business risk; market signals show both strong willingness to buy and a significant enterprise readiness gap. Effective defense requires integrating low-latency enforcement into the runtime path, isolating instruction contexts, and continuously exercising systems with automated adversaries. Commercial winners will combine fine-grained primitives that secure specific failure modes with platform controls that deliver governance, auditing, and performance-compatible enforcement. Security teams should prioritize: (1) immutable separation of system instructions and user data, (2) runtime anomaly detection with immediate containment, and (3) automated red-team pipelines that keep policies current. These steps reduce exposure and create operational resilience while regulations and insurer behaviour increase scrutiny of AI-mediated decision processes.
Are you an insider in the trends or tech industry? We’d love for you to contribute to our content.