Security Infrastructure Report
: Analysis on the Market, Trends, and TechnologiesThe security infrastructure landscape is shifting toward identity-centric, AI-augmented platforms while the internal data shows there are 2,477 companies active in this topic, signaling a large and rapidly expanding supplier base that buyers must rationalize. Market and analyst signals converge: organizations prioritize Identity and Access Management and Zero Trust, accelerate AI for detection and orchestration, and consolidate tooling into unified SASE/SSE stacks to shorten response times and reduce operational strain Accenture. This creates a practical buying imperative: choose platforms that centralize identity, ingest diverse telemetry, and provide verifiable hardware or supply-chain assurances where critical systems demand it.
76 days ago, we last updated this report. Notice something that’s not right? Let’s fix it together.
Topic Dominance Index of Security Infrastructure
To gauge the influence of Security Infrastructure within the technological landscape, the Dominance Index analyzes trends from published articles, newly established companies, and global search activity
Key Activities and Applications
- Identity and Access Management (IAM) and Identity-First controls — continuous authentication, passwordless and just-in-time access to protect human and machine identities across cloud, edge, and OT environments.
- Zero Trust implementation and micro-segmentation — policy driven segmentation that prevents lateral movement and limits blast radius for breaches; applied across enterprise, cloud, and OT networks.
- AI-powered threat detection, triage, and automated response — ML models that correlate telemetry, prioritize events, and execute containment playbooks to shorten mean time to remediate.
- Secure software and MLOps posture — continuous scanning, policy as code, model provenance and inference hardening to protect both applications and AI pipelines, IDC IoT security framework.
- OT/ICS and critical infrastructure protection — network segmentation, data-diode / one-way architectures, and hardware assurance for utilities, transport, and industrial environments.
- Supply-chain and hardware assurance — HSMs, PUFs, provenance tracking and secure firmware to guard against compromised components throughout the lifecycle.
- Converged physical + cyber operations — integrated access control, video analytics, and cyber telemetry to detect insider risk and coordinated multi-vector attacks, ISS video analytics.
- Managed detection, MDR, and SOC automation — outsourcing advanced telemetry ingestion and 24/7 incident handling with AI-assisted playbooks to offset talent gaps.
Emergent Trends and Core Insights
- Identity becomes the primary perimeter. Enterprises place identity verification and continuous authorization at the center of security design, driving large IAM and ITDR investments, IBM.
- AI is a force multiplier and a dual threat. AI reduces detection and response times but also enables faster, more convincing attacks (e.g. AI-assisted phishing); analysts report material increases in AI-driven attacks and plan vendor consolidation to manage complexity JPMorgan Chase, CSET warning on AI risk.
- Platform consolidation and SASE/SSE adoption accelerate. Organizations move from tool sprawl to unified cloud-delivered stacks to centralize telemetry, policy, and enforcement for hybrid work and edge use cases.
- Automation offsets the talent gap. With roughly half of public sector bodies reporting staff shortfalls, automation and AI-copilots become essential to maintain 24/7 monitoring and response World Economic Forum.
- Hardware assurance and data-diode patterns rise for critical systems. Where safety or physical continuity matters, unidirectional controls and tamper-resistant cryptographic anchors gain procurement preference.
- Regulatory and intelligence collaboration increases. NIS2, CISA pilots, and public-private intelligence initiatives force higher baseline controls and faster adoption cycles for resilience investments Critical Infrastructure Protection market, DHS statement on critical infrastructure funding.
Technologies and Methodologies
- Zero Trust Architecture (ZTA) and continuous verification — policy engines, identity graphs, and dynamic authorization enforce least privilege across cloud, network, and OT.
- Secure Access Service Edge (SASE) / Security Service Edge (SSE) — cloud-delivered enforcement that unifies SWG, CASB, ZTNA and FWaaS for distributed workforces, Palo Alto Networks.
- AI/ML for anomaly detection, XDR and automated SOAR playbooks — ingest multi-source telemetry and prioritize high-confidence signals to reduce triage overhead, SentinelOne.
- Hardware roots of trust: HSMs, PUFs, and silicon attestation for key protection and device identity — chosen where long-term confidentiality and provenance matter Securosys, Jmem Tek.
- Data diode and one-way architectures for OT/industrial telemetry — prevent bidirectional compromise of safety networks acquisition coverage by OPSWAT confirms commercial uptake (Dec 2024) OPSWAT press release.
- Micro-segmentation and identity-based network policies — block lateral movement and automate containment using identity graphs Elisity.
- Security as Code, Policy as Code and shift-left DevSecOps — embed detection, secrets management, and compliance checks into CI/CD and MLOps pipelines, Security Innovation.
- Behavioral biometrics and continuous authentication for fraud and access protection — supplement device and credential checks with probabilistic user models.
Security Infrastructure Funding
A total of 182 Security Infrastructure companies have received funding.
Overall, Security Infrastructure companies have raised $6.6B.
Companies within the Security Infrastructure domain have secured capital from 526 funding rounds.
The chart shows the funding trendline of Security Infrastructure companies over the last 5 years
Security Infrastructure Companies
- Saife — Saife builds an endpoint-to-endpoint secure-tunneling platform that centralizes policy and replaces several legacy controls (NAC, VLAN, VPN) with a single policy enforcement plane, enabling secure trusted access over untrusted networks; this maps directly to identity-first and secure access use cases in hybrid and edge deployments.
- PT SYDECO — PT SYDECO packages next-generation firewall, secure VPN servers, and micro-segmentation in an integrated offering tailored for emerging market customers; it emphasizes Zero Trust, contained lateral movement, and simplified deployment for SME and public sector OT cases.
- Fend Incorporated — Fend specializes in physical one-way data diode solutions that protect industrial and critical infrastructure by enforcing unidirectional data flow; that hardware-first pattern answers procurement needs where safety and air-gap assurances are mandated.
- Chip Scan — Chip Scan pursues a hardware-up security posture focused on supply-chain and silicon integrity, applying Zero Trust principles at the chip and firmware level; this work aligns with buyers seeking provable hardware assurance and supply-chain provenance for high-risk deployments.
Get detailed analytics and profiles on 2.5K companies driving change in Security Infrastructure, enabling you to make informed strategic decisions.
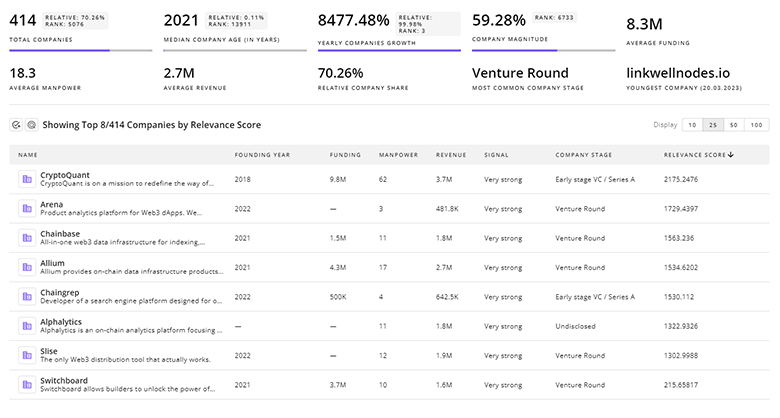
2.5K Security Infrastructure Companies
Discover Security Infrastructure Companies, their Funding, Manpower, Revenues, Stages, and much more
Security Infrastructure Investors
TrendFeedr’s Investors tool provides an extensive overview of 711 Security Infrastructure investors and their activities. By analyzing funding rounds and market trends, this tool equips you with the knowledge to make strategic investment decisions in the Security Infrastructure sector.
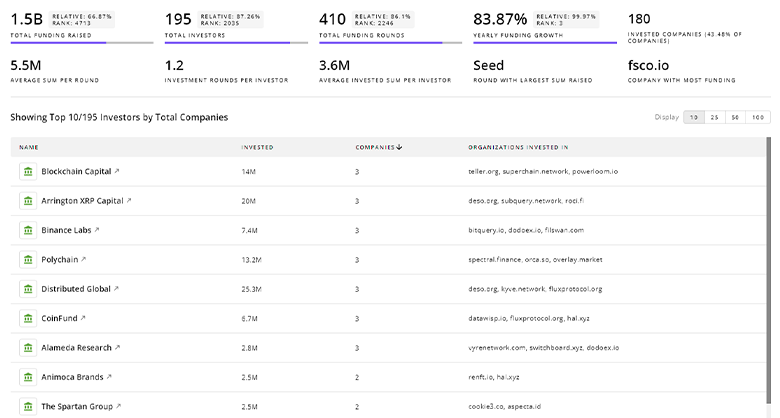
711 Security Infrastructure Investors
Discover Security Infrastructure Investors, Funding Rounds, Invested Amounts, and Funding Growth
Security Infrastructure News
Explore the evolution and current state of Security Infrastructure with TrendFeedr’s News feature. Access 1.7K Security Infrastructure articles that provide comprehensive insights into market trends and technological advancements.
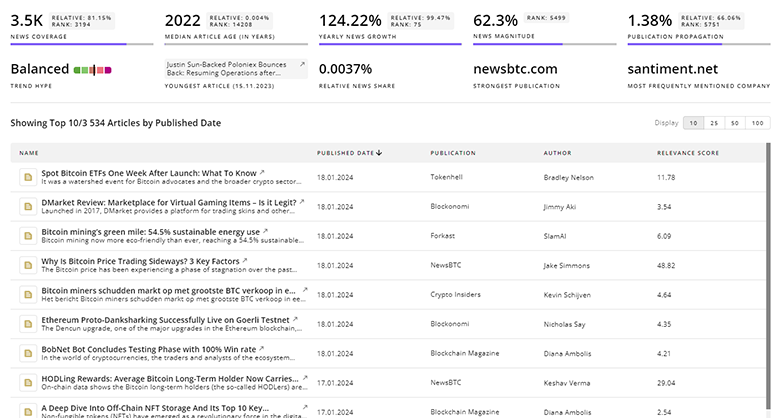
1.7K Security Infrastructure News Articles
Discover Latest Security Infrastructure Articles, News Magnitude, Publication Propagation, Yearly Growth, and Strongest Publications
Executive Summary
Security infrastructure investments now hinge on three coordinated choices: establish identity as the dominant control plane, embed AI where it measurably shortens detection and response, and demand verifiable hardware or supply-chain assurances where service continuity matters. Buyers who rationalize toolsets toward consolidated SASE/SSE platforms and pair those platforms with targeted hardware anchors and automated SOC execution will reduce breach cost and operational friction. Niche vendors that prove non-replicable capabilities at the hardware, identity, or OT levels will remain strategically valuable to platform integrators and to customers with critical resilience requirements.
We're looking to collaborate with knowledgeable insiders to enhance our analysis of trends and tech. Join us!