Intrusion Detection Report
: Analysis on the Market, Trends, and TechnologiesThe intrusion detection market is shifting from signature-first tools to high-fidelity, context-driven detection and managed services, and the internal trend data projects an 18.3% CAGR with a forecasted market value of USD 18,506,750,000 by 2032—a signal that suppliers and buyers will reallocate spend toward analytics, cloud/edge delivery, and services to reduce dwell time and analyst load marketresearch – Intrusion Detection System Market, 2025.
The last update of this report was 85 days ago. If you spot incomplete or incorrect info, please let us know.
Topic Dominance Index of Intrusion Detection
The Topic Dominance Index analyzes the time series distribution of published articles, founded companies, and global search data to identify the trajectory of Intrusion Detection relative to all known Trends and Technologies.
Key Activities and Applications
Behavioral anomaly detection (user, host, flow): building per-user and per-host baselines to detect subtle deviations that indicate insider threats or credential misuse; this activity reduces reliance on static signature updates and addresses zero-day activity patterns.
So what: Organizations that shift budget from signature feeds toward behavior models gain earlier detection of lateral movement and credential abuse, lowering mean time to detect.
Cloud-native workload protection and container/runtime monitoring: instrumenting containers, serverless functions, and host runtimes so detection works where perimeters no longer exist marketresearchfuture - Intrusion Detection System Market, 2025.
So what: Vendors that embed inspection into CI/CD and CSP workflows capture demand from cloud-first enterprises that cannot accept network-only visibility.
Managed detection and response (MDR/MSSP) delivery: 24/7 threat hunting, alert validation, and remediation orchestration for resource-constrained buyers; MDR is a major growth vector in IDPS procurement.
So what: Outsourced detection converts high fixed analyst costs into predictable OPEX, accelerating adoption in SMEs.
Edge and ICS/OT monitoring (including vehicular CAN): lightweight runtime models and protocol-aware detectors tailored to industrial and automotive protocols where latency and safety constraints dominate.
So what: Vendors that demonstrate low-latency, low-footprint inference and protocol semantics will win critical infrastructure and automotive contracts.
Physical perimeter and video analytics fusion: combining radar/LiDAR/thermal/IR with AI video verification to reduce false alarms at high-security sites (airports, data centers).
So what: Integration of physical-sensor fusion with IDPS telemetry produces higher-confidence alarms and tighter operational response SLAs.
Emergent Trends and Core Insights
AI / ML moving from supplement to core scoring: firms invest heavily in proprietary anomaly-scoring models and ensemble stacks to reduce false positives; market investment in ML models rose sharply year-over-year in the company landscape analysis [Company Landscape Report summary].
So what: Differentiation now depends on model precision, drift management, and explainability rather than raw rule counts.
Explainable detection and auditability: security operations demand human-readable rationales (XAI/SHAP) for alerts to speed triage and satisfy compliance/audit requirements MDPI - An Explainable Intelligent 2-Stage Intrusion Detection System.
So what: Products that provide concise, forensically useful explanations reduce analyst time and improve regulator confidence.
Performance optimization and kernel bypass / hardware-aware capture: moving packet inspection closer to NIC/hardware queues or using vector packet processing to reduce latency and overhead.
So what: Device-level efficiency enables high-throughput inspection for service providers and large data centers without unacceptable performance penalties.
Federated learning and privacy-preserving collaboration for edge fleets: collaborative training across customers without raw data exchange is gaining traction in IoT and vehicular networks MDPI - Federated learning for vehicular networks.
So what: MSSPs and platform vendors that operationalize federated models can scale detection knowledge across distributed customers while avoiding data-sharing barriers.
Deception and active mapping: adoption of dynamic decoys and honeypots as a detection source is rising; patents and research show a shift toward systems that lure attackers to reveal intent before mitigation.
So what: Deception provides high-confidence telemetry that complements anomaly systems and yields rich attacker tradecraft data.
Technologies and Methodologies
Graph Neural Networks (GNNs) and spatio-temporal models for multi-entity correlation: used to connect users, processes, and flows so detectors reason about intent and attack paths MDPI - Dynamic Graph and LLM–Semantic Enhanced Spatiotemporal GNN.
Impact: GNNs increase precision on multi-stage attacks (recon → lateral movement) by modelling relationships rather than isolated events.
Ensemble and hybrid stacks (deep feature extractors + tree/boosting classifiers): academic and benchmark work shows ensembles often exceed single-model accuracy, which reduces false alarms in heterogeneous traffic MDPI - Autoencoder–Dense–Transformer Neural Network Model.
Impact: Ensembles provide practical production stability and easier tuning for imbalanced attack datasets.
Extended Detection and Response (XDR) and X-plane consolidation: fusing endpoint, network, identity, and cloud telemetry into a single investigative plane to reduce fragmentation and accelerate root cause analysis.
Impact: XDR reduces alert fatigue by prioritizing attacker-centric narratives instead of siloed noisy alerts.
Edge inference and lightweight models for constrained devices: pruning, quantization, and optimized feature sets enable IDS functionality on gateways, OT devices and CAN bus monitors MDPI - Design and Validation of a Lightweight Intrusion Detection Algorithm.
Impact: Edgeable models enable faster mitigation and preserve connectivity for remote and safety-critical deployments.
Integration of deception and active response playbooks: detection systems that trigger controlled decoys and automated containment reduce the need for immediate human action while gathering forensic telemetry.
Impact: Active detection shortens attacker dwell time and improves incident understanding.
Intrusion Detection Funding
A total of 286 Intrusion Detection companies have received funding.
Overall, Intrusion Detection companies have raised $7.4B.
Companies within the Intrusion Detection domain have secured capital from 727 funding rounds.
The chart shows the funding trendline of Intrusion Detection companies over the last 5 years
Intrusion Detection Companies
Octopyder
Octopyder focuses on low-footprint network sensors and a managed analytics overlay geared to industrial clients. The company emphasizes protocol-aware parsers for ICS/OT networks to surface semantic anomalies that generic NIDS miss. Their product targets sites that cannot tolerate latency or heavy processing at the core, offering field-deployable appliances plus centralized incident correlation.Spiderweb Labs
Spiderweb Labs develops edge IDS modules that run on gateways and automotive ECUs using compact, explainable models. They combine entropy-based detectors for CAN bus anomalies with a cloud service for model refresh and threat sharing. The firm wins deals where operators require deterministic performance and evidence for audits.Cerber.tech
Cerber.tech provides a multi-sensor perimeter solution that fuses thermal, LiDAR, and AI video verification to reduce false alarms in harsh environments. Their stack emphasizes adaptive thresholds and sensor hygiene routines to maintain uptime across weather and animal activity. Customers include critical infrastructure sites that demand high-accuracy physical intrusion alerts tied to SOC workflows.Cybersense.ai
Cybersense.ai builds NIDS/NDR modules that use unsupervised representation learning to detect novel lateral-movement patterns in east-west traffic. They position their product as a high-sensitivity detector with analyst-facing explainability features to speed triage. Their target buyers are mid-market cloud operators that need rapid deployment without large security teams.Honeymonitor
Honeymonitor supplies managed deception services and dynamic honeypot orchestration that integrates with existing SIEM/XDR tooling. The product automates decoy deployment and harvests attacker telemetry for ML model retraining and threat intelligence feeds. This service suits organizations that want high-confidence alerts plus forensic data without building internal deception expertise.
TrendFeedr’s Companies tool is an exhaustive resource for in-depth analysis of 3.6K Intrusion Detection companies.
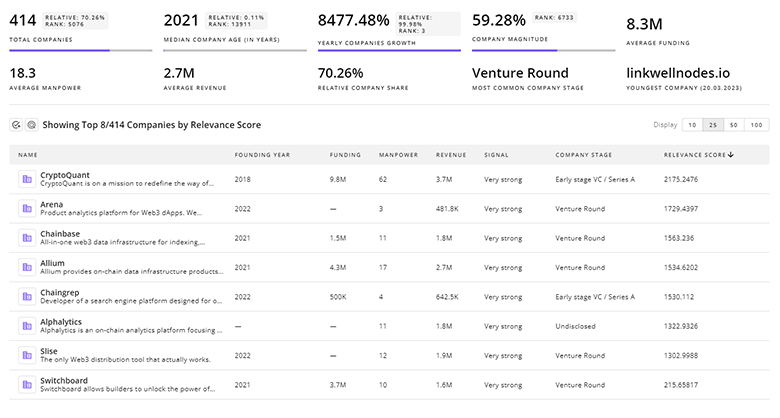
3.6K Intrusion Detection Companies
Discover Intrusion Detection Companies, their Funding, Manpower, Revenues, Stages, and much more
Intrusion Detection Investors
The TrendFeedr’s investors tool features data on 703 investors and funding activities within Intrusion Detection. This tool makes it easier to analyze complex investment patterns and assess market potential with thorough and up-to-date financial insights.
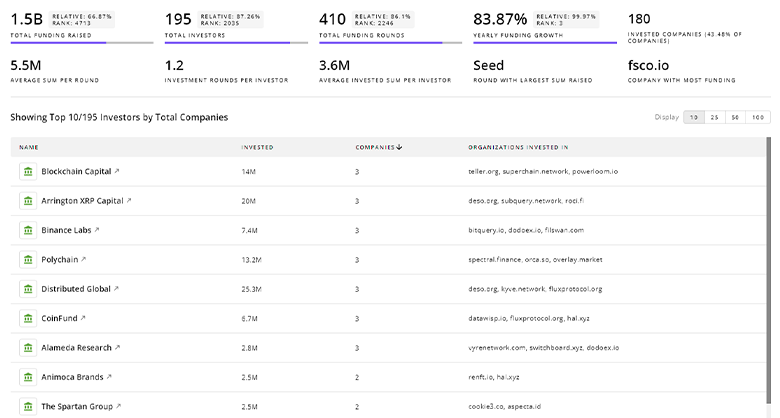
703 Intrusion Detection Investors
Discover Intrusion Detection Investors, Funding Rounds, Invested Amounts, and Funding Growth
Intrusion Detection News
Stay ahead of the curve with Trendfeedr’s News feature. The tool provides access to 6.4K Intrusion Detection. Navigate the current business landscape with historical and current Intrusion Detection data at your fingertips.
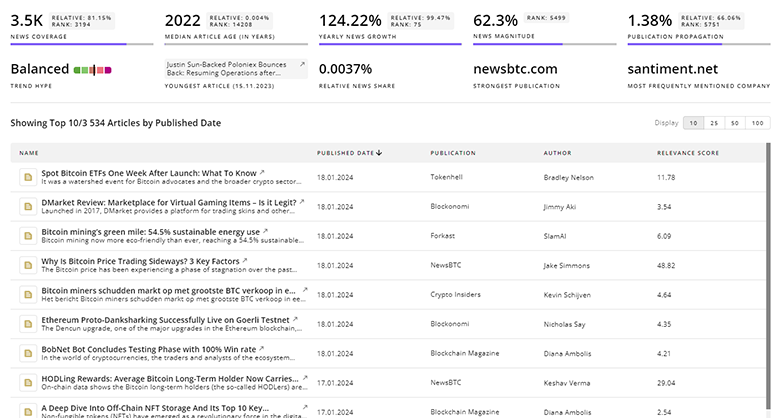
6.4K Intrusion Detection News Articles
Discover Latest Intrusion Detection Articles, News Magnitude, Publication Propagation, Yearly Growth, and Strongest Publications
Executive Summary
Detection is shifting from point solutions to multi-domain, analytics-first platforms delivered as services. The business implication is clear: buyers will favor vendors that combine precise, explainable ML with deployment flexibility (edge, cloud, on-premises) and operational services (MDR, deception orchestration). Technology leaders will be those who reduce false positives through entity context (GNNs, behavioral baselines), minimize processing overhead via hardware-aware capture, and provide verifiable decision trails for compliance and SOC efficiency. Vendors that fail to embed explainability, low-latency inference, and service platforms will face pressure as buyers trade capital expense and headcount for integrated, high-confidence detection outcomes.
If you’re an expert in trends or emerging tech, we invite you to contribute to our insights.